10 Cybersecurity Challenges MSPs Face in 2025: and How Advanced Capabilities Can Drive Growth
The Managed Services Provider (MSP) industry is at a crossroads. Managed service providers (MSPs) face increasingly complex cybersecurity challenges, with threats evolving faster than ever and client expectations rising. For MSP CEOs and business owners, navigating these challenges isn’t just about survival - it’s about seizing the opportunity to grow.
The stakes have never been higher. The average cost of a data breach reached $4.88 million in 2024, a 10% increase from the previous year, while global fines for data privacy violations have exceeded $7.3 billion since 2020. Addressing these challenges is critical to protecting client trust and ensuring sustainable growth.
But here’s the opportunity: By adding advanced cybersecurity capabilities to your offerings, MSPs can turn these hurdles into revenue drivers. Whether by transitioning to MSSP capabilities or partnering with a trusted MSSP to provide high-value security services, MSPs can meet client needs while unlocking incremental revenue streams.
This guide explores the top 10 cybersecurity challenges MSPs face in 2025 and offers actionable insights to help you strengthen your security offerings, retain clients, and grow your business - no matter your approach.

1. Combatting the Rising Sophistication of Cyber Threats in the Cybersecurity Landscape

Cyber attackers are deploying increasingly advanced techniques, leveraging artificial intelligence to bypass defenses and exploit vulnerabilities. AI-driven solutions are transforming the cybersecurity landscape for MSPs by enhancing threat detection and incident management through automation and predictive analysis.
Ransomware, malware, and phishing remain top concerns for MSPs, with new variants emerging daily. For example, AI-driven phishing attacks in 2024 demonstrated how attackers can convincingly mimic trusted entities, making it harder for even vigilant users to identify scams.
While these threats present significant risks, they also offer MSPs an opportunity to grow. By proactively addressing these challenges, you can upsell advanced cybersecurity capabilities, such as Endpoint Detection and Response (EDR), and position yourself as a trusted partner for your clients.
Key Action Steps:
- Invest in Real-Time Threat Detection Tools: Deploy AI-powered solutions to identify and neutralize threats as they occur.
- Upsell EDR as a Premium Service: Offer clients enhanced endpoint protection as an essential layer of defense against ransomware and malware.
- Develop a Proactive Incident Response Plan: Provide incident response as a value-added service to ensure your clients are prepared for worst-case scenarios.
By staying ahead of these threats and introducing high-value solutions, you can both protect your clients and unlock incremental revenue opportunities.
2. Why a Strong Security Posture is a Non-Negotiable for MSPs

A strong security posture isn’t just about defense - it’s a foundation for growth. It protects your clients’ sensitive data, minimizes risks of breaches, and builds trust. For MSPs, maintaining this trust is essential to retaining clients and unlocking upsell opportunities for advanced security services.
In today’s landscape, clients expect more than basic IT support. By strengthening your security posture with enhanced security measures, you can position yourself as their go-to provider for comprehensive, high-value cybersecurity services.
Key Action Steps:
- Implement Multi-Layered Defenses: Deploy advanced tools like firewalls, intrusion detection/prevention systems (IDPS), and endpoint protection.
- Offer Ongoing Security Audits: Provide regular security assessments as a premium service to help clients stay compliant and reduce risks.
- Promote Security Awareness Training: Package training sessions to educate clients on phishing and other common threats, turning them into proactive participants in their own protection.
A robust security posture isn’t just about reducing risks - it’s a strategic advantage that opens doors to new revenue streams while enhancing client loyalty.
3. Navigating Stricter Regulatory Compliance

The rise in data privacy regulations like GDPR, HIPAA, and CCPA has made compliance more complex and demanding. Non-compliance can result in substantial fines, such as the $1 billion penalty paid by U.S. credit reporting agency Equifax after a 2017 data breach affecting 150 million consumers. Globally, data privacy violations have led to over $7.3 billion in fines since 2020, and regulators are showing no signs of slowing down, highlighting the significant risk associated with non-compliance.
For MSPs, understanding and adhering to these requirements is critical to retaining enterprise clients and building trust. But compliance isn’t just a burden - it’s an opportunity to differentiate your services and create new revenue streams through compliance-focused offerings.
Key Action Steps:
- Offer Compliance Audits as a Service: Help clients identify vulnerabilities and meet regulatory standards with regular audits.
- Leverage Automation Tools: Simplify tracking and reporting with compliance management software to reduce manual effort and increase efficiency.
- Bundle Compliance Support: Include compliance assistance in premium service packages to provide more value and grow your MRR.
By proactively addressing compliance, MSPs can protect clients, avoid costly penalties, and position themselves as trusted advisors - unlocking new growth opportunities in the process.
4. Overcoming the Cybersecurity Talent Shortage Amid Emerging Threats

The global shortage of cybersecurity professionals continues to challenge MSPs. Including employees in the cybersecurity conversation is crucial to mitigate vulnerabilities. Finding skilled talent is not only difficult but often prohibitively expensive, making it harder to meet client demands and expand services. This shortage can limit growth, leaving many MSPs struggling to deliver the level of security their clients need.
But the talent gap also presents an opportunity. By outsourcing cybersecurity capabilities or leveraging automation, MSPs can expand their offerings without adding full-time staff - boosting profitability and scalability.
Key Action Steps:
- Partner with MSSPs or Cybersecurity Experts: Collaborate with managed security service providers to fill expertise gaps and offer high-value services like 24/7 threat monitoring.
- Leverage AI and Automation: Deploy tools that automate routine tasks like threat detection, reporting, and patch management, freeing up internal resources.
- Upskill Existing Teams: Invest in targeted training programs to enhance your team’s cybersecurity skills and reduce reliance on external hires.
By combining external partnerships, automation, and training, MSPs can not only address the talent shortage but also scale their services and grow revenue without overextending their resources.
5. Tackling Integration Challenges in Complex Environments

As MSPs manage diverse client environments, integrating disparate technologies into a cohesive cybersecurity framework can feel like solving a never-ending puzzle. Poorly integrated systems not only create inefficiencies but also leave critical security gaps that could put client data at risk, making them vulnerable to cybersecurity threats.
However, seamless integration can become a differentiator. By adopting advanced tools and standardizing processes, MSPs can streamline operations and position themselves as experts in managing complex environments.
Key Action Steps:
- Use Centralized Management Platforms: Leverage tools like Security Information and Event Management (SIEM) systems to oversee and integrate multi-client environments effectively.
- Standardize Tools and Processes: Reduce complexity by implementing a consistent cybersecurity stack across your client base.
- Offer Integration as a Service: Package integration solutions as a premium offering, helping clients unify their systems while generating incremental revenue.
By addressing integration challenges proactively, MSPs can ensure stronger security, improve efficiency, and create opportunities to upsell value-added services.
6. Striking the Balance Between Costs and Value
Cybersecurity tools and services are becoming increasingly expensive, creating a challenge for managed service providers (MSPs) to deliver high-value solutions while maintaining profitability. Clients often demand top-tier protection but may be hesitant to pay premium rates, putting pressure on MSPs to find the right balance.
This challenge also presents a growth opportunity. By bundling high-value cybersecurity services into scalable packages, MSPs can enhance client satisfaction while boosting recurring revenue.
Key Action Steps:
- Evaluate and Optimize Toolsets: Regularly audit your existing tools to eliminate redundancies and focus on solutions that deliver the highest ROI.
- Offer Tiered Service Packages: Create customizable service levels, allowing clients to scale their cybersecurity investment as their needs grow.
- Bundle High-Margin Services: Combine advanced offerings like managed detection and response (MDR) or compliance management into premium packages to drive incremental revenue.
By focusing on cost-effective, value-driven solutions, MSPs can maintain profitability while meeting the evolving needs of their clients.
7. Staying Competitive Against Larger MSPs

Larger MSPs dominate the market with their extensive resources, comprehensive services, and ability to scale rapidly. For smaller MSPs, competing with these giants can feel like an uphill battle. However, size isn’t everything. By focusing on specialization and personalized service, smaller MSPs can differentiate themselves and build stronger client relationships. Incorporating threat intelligence into your services can also provide a significant advantage by enabling proactive cybersecurity measures.
Key Action Steps:
- Target Niche Markets: Focus on specific industries like healthcare, finance, or retail where specialized expertise can set you apart.
- Leverage Success Stories: Use testimonials and case studies to showcase how your tailored approach delivers results.
- Upsell Premium Cybersecurity Services: Offer advanced solutions like 24/7 threat monitoring or compliance management to compete on value rather than size.
By honing your unique strengths and offering high-margin services, smaller MSPs can carve out a competitive edge and win in a crowded marketplace.
8. Educating Clients to Reduce Risk

Many cybersecurity breaches stem from client-side vulnerabilities like weak passwords, phishing scams, and outdated software. These vulnerabilities expose clients to significant cybersecurity threats. While these behaviors can frustrate MSPs, they also represent an opportunity to add value. By offering security awareness training as a service, MSPs can reduce client risk while generating incremental revenue.
Key Action Steps:
- Provide Security Awareness Training: Offer regular training sessions on topics like phishing detection, password management, and safe browsing habits.
- Run Mock Phishing Campaigns: Simulate phishing attacks to educate clients in real-time and measure improvements in their security awareness.
- Bundle Awareness Programs with Cybersecurity Services: Position training as part of a premium package to enhance client protection and create an upsell opportunity.
Educated clients are less likely to fall victim to attacks, making them better partners and strengthening the value of your services.
9. Scaling Cybersecurity Services to Meet Demand

As MSPs grow, so do their clients’ demands for scalable, robust cybersecurity solutions. Quantum computing is poised to disrupt traditional encryption methods, necessitating quantum-ready encryption strategies. Handling larger accounts or a broader customer base often strains existing resources, making it challenging to maintain service quality. But with the right approach, scaling cybersecurity services can unlock opportunities to take on higher-value clients and increase recurring revenue.
Key Action Steps:
- Adopt Scalable Cloud-Based Solutions: Use platforms like Secure Cloud Solutions Management (SCSM) to handle growing workloads without requiring significant upfront investments.
- Standardize Processes Across Clients: Streamline operations with consistent workflows and a unified cybersecurity stack to enhance efficiency.
- Bundle Scalable Services for Larger Accounts: Offer premium, flexible packages designed to meet the needs of enterprise clients, driving higher revenue.
By focusing on scalable solutions and tailored packages, MSPs can manage growth effectively while positioning themselves to attract and retain larger, higher-margin accounts.
10. Prioritizing Network Security in a Remote-First World

The shift to remote work and bring-your-own-device (BYOD) policies has significantly expanded the attack surface for cybercriminals. Unsecured networks, personal devices, and decentralized access points make robust network security more critical than ever. For MSPs, strengthening network security is not only essential for protecting clients but also an opportunity to upsell premium security solutions.
Key Action Steps:
- Deploy Advanced Network Security Tools: Offer solutions like virtual private networks (VPNs), intrusion detection/prevention systems (IDPS), and endpoint detection and response (EDR) as premium services.
- Implement Multi-Factor Authentication (MFA): Enhance access control for clients by including MFA in your service packages.
- Offer Remote Security Assessments: Conduct regular vulnerability scans for clients with remote teams, bundling this as part of a value-added service.
By addressing the unique challenges of remote work environments, MSPs can protect their clients while creating opportunities to deliver high-margin security services.
Conclusion

The cybersecurity landscape is more complex than ever, and MSPs face mounting challenges in staying ahead. From meeting stricter compliance requirements to scaling services and addressing increasingly sophisticated threats, these issues can feel overwhelming. But with the right strategy, they also present an opportunity to grow.
The key to thriving in 2025 and beyond? Evolving your MSP into an MSSP.
By adding advanced cybersecurity capabilities - like 24/7 monitoring, endpoint detection and response (EDR), and compliance management - you can upsell high-value services, generate incremental revenue, and position yourself as a trusted partner for your clients.
Top 3 Solutions for MSP Growth:
- Upsell Advanced Cyber Capabilities: Introduce premium services like MDR and cloud security to enhance your offerings and boost recurring revenue.
- Transition to MSSP Capabilities: Offer specialized, high-margin security services to meet client needs and differentiate yourself in a crowded market.
- Partner with Experts: Collaborate with trusted advisors like CyVent to seamlessly integrate advanced solutions without overextending your resources.
For a real-world example of how this transformation works, read our Symbits case study. Learn how they strengthened their cybersecurity, retained major clients, and achieved 35% cost savings with the right approach.
Ready to Transform Your MSP into an MSSP? Let CyVent help you stay ahead.
Positioning your MSP as a trusted cybersecurity leader starts here. At CyVent, we specialize in helping MSPs bridge gaps in their cybersecurity offerings, transition to MSSP capabilities, and unlock new revenue streams.
Contact us for a free confidential consultation. and discover how we can help you scale seamlessly, grow your revenue, and build lasting client trust.
Inside Doxbin: How Leaked Data Is Shaping the Dark Web in the Age of AI

When we think about the challenges of digital privacy, few incidents have been as infamous as the Doxbin data leaks. Doxbin, a controversial platform known for enabling doxing—publicly exposing personal information without consent—has become a cautionary tale about the dangers of unchecked online activity.
Yet, the lessons from Doxbin aren’t confined to the past. Today, advancements in artificial intelligence (AI) have transformed the dark web’s landscape, making the risks even greater. As we grapple with the evolving threats posed by AI-enhanced cybercrime, it’s crucial to reflect on how incidents like Doxbin shape modern cybersecurity strategies.
This article provides a comprehensive understanding of the impact of AI on doxing and offers practical solutions to protect personal and professional data in an increasingly digital world.
Key Takeaways
- Doxbin’s legacy as a doxing hub continues to raise awareness about privacy violations and the importance of proactive data protection.
- AI is amplifying the risks posed by platforms like Doxbin, enabling faster, more precise, and automated attacks that endanger individuals and businesses alike.
- SMBs must act now by adopting AI-driven defenses to mitigate threats and safeguard sensitive information.
The Doxbin Phenomenon and Its Modern Implications

Doxbin operates as a paste site where users share personally identifiable information (PII) such as names, addresses, social security numbers, and more. Its existence highlights persistent legal and ethical challenges in balancing privacy rights with accountability.
The platform gained notoriety for its role in targeting individuals for personal vendettas or ideological disagreements. Although Doxbin’s activity peaked several years ago, the issues it surfaced remain deeply relevant today, especially as AI supercharges the methods used for doxing.
How AI Fits In
AI tools are reshaping the way cybercriminals gather, analyze, and weaponize information. Where Doxbin users once relied on manual efforts to scrape and compile data, AI now enables:
- Automated data scraping: Extracting PII from publicly available sources at an unprecedented scale.
- Social engineering at scale: Crafting highly personalized phishing emails or impersonation attacks.
- Predictive targeting: Using AI algorithms to identify vulnerabilities in potential victims.
The implications are clear: incidents like Doxbin are no longer isolated threats—they’ve set the stage for an era of AI-driven cybercrime.
What is Doxbin?

Doxbin is a dark web platform where users share sensitive personal data, including social security numbers, email addresses, healthcare records, and bank account information, without consent. This practice, known as doxing, has devastating consequences for victims, ranging from online harassment to real-world dangers like swatting or identity theft.
Despite facing multiple shutdowns, the site has managed to persist, becoming notorious for its resilience. Users often regroup on platforms like Telegram to exchange information and stay under the radar. This ongoing cycle underscores the complexities of tackling dark web activities, a challenge now intensified by the advent of AI technologies.
What is Doxing?
Definition of Doxing
Doxing is the act of publicly revealing personally identifiable information about an individual or organization without their consent. This can include sensitive information such as real name, home address, workplace, phone number, financial details, and other personal data. The intent behind doxing is often malicious, aiming to harass, intimidate, or harm the victim.
Brief History of Doxing
The term “doxing” originated in the hacker world in the 1990s, where anonymity was considered sacred. Hackers would “drop docs” (documents) on a rival, exposing their real identity. However, with the rise of social media and online platforms, doxing has expanded beyond the hacker community. Today, it refers to the exposure of personal information online, often to a much broader audience, making it a widespread issue in the digital age.
Examples of Doxing
Doxing can take many forms, including the exposure of personal details, financial information, and online activity. For instance, a person’s social media accounts may be hacked, and their personal information shared publicly. Another example is when domain registration information is used to reveal someone’s physical address. These actions can lead to severe consequences, such as harassment, identity theft, or even physical harm.
AI’s Role in Modern Doxing
AI has dramatically evolved the tactics used in doxing. While traditional methods involved manually piecing together data from disparate sources, AI enables cybercriminals to operate with far greater speed and efficiency. Key developments include:
1. Enhanced Data Aggregation
AI algorithms can sift through massive datasets—including leaked information on forums like Doxbin—and compile detailed victim profiles in minutes. This automation means that even smaller-scale attacks can target hundreds of individuals simultaneously.
AI can also assist in tracking IP addresses doxers use, revealing physical locations and enabling further data collection through social engineering.
2. AI-Driven Social Engineering on Social Media Accounts
By analyzing behavioral patterns and online activity, AI tools can generate highly convincing phishing messages or impersonations, increasing the likelihood of success. This technique is particularly dangerous for SMBs, where employees may inadvertently expose sensitive business data.
3. Scalable Threats
Doxbin once exposed individual victims, but AI allows attackers to scale operations. For example, a single AI-enabled tool can scour multiple platforms, extract PII, and deploy targeted attacks en masse.
How Does Doxing Work?
Tracking Usernames and Online Activity
Doxers often use various methods to gather and share personal information about someone. One common method is tracking usernames and online activity. By using the same username across multiple platforms, individuals can inadvertently create a trail of breadcrumbs that doxers can follow to gather more information. Additionally, doxers may use online tools to track IP addresses, which can be linked to a person’s physical location. This information can then be used to gain access to a person’s financial accounts, credit card information, and other sensitive data.
To protect against doxing, individuals should consider using different usernames for different platforms, hide domain registration information, and create separate email accounts for various online activities. It’s also advisable to use services that can mask your IP address and involve your internet service provider if you suspect you’re being targeted. In some cases, a reverse mobile phone lookup can be used to gather more information about the doxer, helping to track them down and involve law enforcement if necessary.
The Impact of Data Leaks on Personal Details and Security

Leaked data on platforms like Doxbin severely compromises personal and professional security. Once exposed, information such as names, addresses, email accounts, and social security numbers often persists on cached pages, making it nearly impossible for victims to regain control. This can lead to dire consequences, including:
- Identity Theft: Fraudsters exploit stolen data like social security numbers to open fraudulent accounts or access existing financial records.
- Swatting: AI-driven malicious reports can escalate to potentially deadly encounters with law enforcement.
- Business Risks: SMBs face reputational damage, legal liability, and financial losses when sensitive data belonging to employees or customers is leaked.
Doxbin has demonstrated how doxers can track usernames across multiple platforms to build comprehensive profiles on their targets. The real-world impacts of these leaks extend beyond online harassment, leading to financial ruin, emotional distress, and even social isolation for victims.
Types of Information Exposed
The information shared on Doxbin includes critical personal details that amplify the risks of doxing:
- Personally Identifiable Information (PII): Names, addresses, email accounts, and affiliations.
- Sensitive Financial Data: Social security numbers and banking information that enable identity theft.
- Other Exploitable Data: Leaked email accounts used for spam, phishing, or unauthorized access attempts.
A Wake-Up Call for Better Protection
Doxbin is a chilling reminder of the far-reaching consequences of data exposure. While some states have passed laws to address doxing, the anonymous nature of perpetrators still makes legal recourse difficult. Victims not only endure financial and emotional strain but also experience a long-term erosion of trust in digital interactions.
Analyzing the Most Recent Doxbin Data Breach

The most recent data breach on Doxbin occurred on January 5, 2022, when a cybercriminal publicly shared sensitive information from the platform on a forum. This breach exposed a substantial amount of data, including over 41,000 user credentials such as usernames, email addresses, and passwords. The leak highlighted the vulnerabilities within Doxbin’s infrastructure and the risks associated with storing sensitive data on such platforms.
The breach’s significance lies not only in the volume of data exposed but also in the community it affected. Over 300,000 registered users on Doxbin were potentially impacted, although the exact number of compromised accounts remains undisclosed. This incident underscores the importance of robust security measures and the constant threat posed by malicious actors in the cybercrime landscape.
Internal Conflicts and Retaliation
Doxbin has a history of internal conflicts that have led to significant repercussions for its users and administrators. Ownership changes and disputes often result in retaliatory actions, as seen when Nachash leaked Doxbin’s logs after taking over as the admin. These internal conflicts highlight the volatile nature of the platform and the risks involved in its operation.
The contentious environment within Doxbin has led to allegations and counter-allegations among users and former administrators, further complicating the site’s dynamics. These conflicts can escalate into actions that compromise the security of family members and associates, illustrating the far-reaching consequences of the platform’s activities.
Understanding these internal conflicts sheds light on the broader impact of Doxbin's activities.
Techniques and Tools Used in Doxing (Then and Now)
.png?width=893&height=502&name=Techniques%20and%20Tools%20Used%20in%20Doxing%20(Then%20and%20Now).png)
Doxing has evolved significantly since Doxbin first emerged. Today, it’s a combination of traditional methods and cutting-edge AI tools:
Traditional Techniques
- Social media stalking to gather personal details.
- Public record searches to identify home addresses and affiliations.
AI-Enhanced Tactics Including Reverse Mobile Phone Lookup
- Hacking Automation: AI tools can identify weak passwords or insecure networks faster than human attackers.
- Data Correlation: Machine learning algorithms link disparate pieces of information to build highly accurate victim profiles. In the event of exposure, it is crucial to contact your credit card provider to cancel compromised cards and protect your financial information.
- Deepfake Technology: AI-generated impersonations add a new layer of sophistication to social engineering.
Mitigating Risks: Cybersecurity Best Practices for SMBs

In the face of these evolving threats, SMBs must adopt proactive cybersecurity measures. Here’s how AI can work as a defense rather than a threat:
AI for Threat Detection
Modern AI tools can analyze network activity in real time, flagging unusual behavior and potential breaches. This capability allows SMBs to stay one step ahead of attackers.
Cyber Hygiene Fundamentals: Create Separate Email Accounts
- Use strong, unique passwords and enable two-factor authentication.
- Regularly monitor the web (including dark web platforms) for signs of exposed data.
- Train employees on phishing awareness and safe online practices.
Summary
The Doxbin saga may have started years ago, but its lessons are more critical than ever. As AI transforms the cybersecurity landscape, threats like doxing are becoming more scalable and harder to combat. The persistence of exposed data and the rise of AI-driven attacks highlight the urgent need for proactive protection.
For SMBs, safeguarding sensitive information is no longer optional—it’s essential. By understanding these evolving risks and taking action, businesses can protect their operations, reputations, and customers.
Partner with Experts

At CyVent, we specialize in tailored cybersecurity solutions to address today’s most pressing threats. Our AI-powered tools and expert guidance help you fortify your defenses, protect your data, and stay ahead of attackers.
Schedule a confidential call with CyVent today to discuss how we can help your business navigate the complexities of modern cybersecurity with confidence.
Frequently Asked Questions

What is Doxbin?
Doxbin is a platform on the dark web where users share personal information without consent, leading to significant privacy and security risks.
What types of information are typically exposed on Doxbin?
Doxbin typically exposes sensitive information such as names, addresses, social security numbers, emails, and healthcare histories. This poses significant privacy and security risks.
What are the real-world consequences of doxing?
Doxing can lead to severe consequences such as identity theft, swatting, and considerable emotional and psychological distress for those targeted. These outcomes underscore the serious risks associated with exposing personal information online.
How has AI changed doing?
AI enables faster, more precise attacks by automating data aggregation, social engineering, and predictive targeting.
How can individuals protect themselves from being doxed?
To protect yourself from being doxed, use strong, unique passwords and enable two-factor authentication on your accounts. Additionally, regularly monitor your online presence to identify and address potential threats.
What steps can SMBs take to protect themselves?
SMBs can adopt AI-powered threat detection tools, enforce strong cyber hygiene practices, and partner with experts like CyVent for tailored solutions.
What are the legal implications of doxing?
Doxing can lead to criminal charges in some jurisdictions, highlighting the urgent need for updated regulations to effectively address privacy violations. It is crucial to understand the legal landscape in your area to avoid potential repercussions.
If you're worried about protecting your personal information and navigating the complexities of online privacy, consider exploring our expert services. We offer comprehensive solutions tailored to safeguard your digital identity and prevent unauthorized access to your personal data. Learn more about our services here.
Microsoft is planning to enable Multi-Factor Authentication (MFA) directly in its Outlook app for many 365 business users.
MFA is a vital tool to help protect your online accounts from cyber criminals. It works by generating a second, single-use passcode every time you log into an account. It’s usually sent to an authenticator app on your phone that you have to download and set up first.
Security codes can also be sent via SMS text message, by a phone call, or you might be given a special USB key to plug into your computer.
The process is often made quicker by using a biometric login like your fingerprint or face ID. It’s a minor chore, but the protection it offers far outweighs the couple of extra seconds it takes to access your account.
Microsoft isn’t so sure about those extra seconds, though. If the tech giant can save you that time, it’s going to do it. That’s why it’s looking to streamline MFA for Microsoft 365 business accounts.
It’s rolling out the improvement by building MFA directly into the Outlook app in a feature called Authenticator Lite. Until now, it’s relied on a separate authenticator app or sending login codes.
There’s no news yet for those of us who want faster authentication on our personal PCs. If Microsoft does announce plans to make this feature available to more hardware or operating systems, we’ll update you with any news.
If you don’t already use MFA for your apps and online accounts, we recommend that all businesses implement it as soon as possible. The additional security it offers protects against the vast majority of today’s cyber threats.
For more help and advice about implementing MFA or getting the best from Microsoft 365, just get in touch.
Published with permission from Your Tech Updates.

If we talk about ‘bots’ you’d be forgiven for thinking of the amazing AI chatbots that have been all over the news lately.
But this isn’t a good news story. Bots are just automated programs, and bot malware is a worrying new security risk you need to defend your business against.
Malware bots are particularly dangerous because they steal whole user profiles – that’s a complete snapshot of your ID and settings. This potentially allows cyber crooks to bypass strong security measures like Multi-Factor Authentication (MFA).
Usually, if a criminal steals your username and password, they still can’t access your account because they don’t have access to your MFA authentication method. But with your whole profile available to them, using your cookies and device configurations, they can trick security systems and effectively switch off MFA.
Once profile information is stolen, it’s sold on the dark web for as little as $5.
And it’s not even super-sophisticated cyber criminals deploying this technique. Just about anyone can obtain your details and use them for phishing emails, scams, and other criminal activity.
Since 2018, 5 million people have had 26.6 million usernames and passwords stolen, giving access to accounts including Microsoft, Google, and Facebook.
All this means there are things you need to do – right now – to keep your profiles and your business protected from bot malware.
- Update your antivirus software and keep it on at all times.
- Use a password manager and Multi-Factor Authentication to keep your login credentials safer
- And encrypt all your files so that, if anyone does access your profile, there’s very little to steal.
These are the things we help our clients with every day. If we can help you, just get in touch.
Published with permission from Your Tech Updates.

Have you ever tried to buy tickets for a huge event and found that the seller’s website has collapsed under the weight of thousands of people all trying to do the same thing at the same time?
The ticket site falls over – usually temporarily – because the server is overloaded with traffic it doesn’t have the capacity for.
Criminal Distributed Denial of Service attacks – DDoS, for short – exploit the same principle.
When a DDoS attack targets a business, it floods it with internet traffic in an attempt to overwhelm the system and force it to fail.
This results in the business and its customers being unable to access services. That may trigger a temporary failure, or it could be more serious. Last year, the average DDoS attack lasted 50 minutes.
That may not sound like a long time, but it’s enough to create angry customers, or to bring business to a grinding halt. And downtime can be costly.
The really bad news is that DDoS attacks are not only lasting longer, but they’re becoming bigger, more sophisticated and more common.
Recently, the biggest ever reported DDoS attack was reportedly blocked. At its peak, it sent 71 million requests per SECOND to its target’s servers. Prior to that, the biggest reported incident stood at 46 million requests per second.
Worse still, more businesses are reporting being targeted by DDoS attacks where criminals are demanding huge ransoms to stop the attack.
What does this mean for you?
It’s important you check all your security measures are up-to-date and working as they should be. Are your firewalls up to the task, with DDoS monitoring and prevention tools set up? And is your team fully aware of the importance of staying vigilant?
We can help make sure your business stays protected. Just get in touch.
Published with permission from Your Tech Updates

To protect your home from an intruder you make sure your doors and windows are all locked and secured. You might go further: build a fence around the perimeter, perhaps even get an angry-looking dog to stand guard.
But there’s no point going to all that effort if someone’s already broken in and set up camp in the basement.
Yet that’s the security policy of thousands of big businesses trying to protect their data from cyber criminals.
They do many of the right things. They invest in security software. They take a strong, multi-layered approach to security – including all the things we recommend, like multi-factor authentication, encryption, reliable backup systems and staff training.
But they don’t pay enough attention to detection and response. That involves constantly scanning systems for any sign that a crook may have gained entry somewhere, and having a process to stop an attack in its tracks.
A new study shows that only a third of businesses place detection as their main priority, while two thirds say prevention is their primary focus.
That means, they could be building 10-foot walls around their systems with intruders already inside.
In-house security teams might be super-confident in the security measures they’ve put in place. But the data suggests that they’re being too complacent. The study reveals that more than eight in ten businesses experienced more than one data breach last year – even with good security in place.
Criminals are constantly finding ways to evade security. That tells us that we need to take a rounded approach, with strong prevention AND detection policies providing the best protection against today’s determined criminals.
If you need world-class security, get in touch today.
Click here to book a call and speak with one of our experts .
5 Best Managed Detect and Response (MDR) Solutions (Key Features, Pros, and Cons)
%20Solutions%20(Key%20Features%2c%20Pros%2c%20and%20Cons).jpg?width=2048&height=1190&name=5%20Best%20Managed%20Detect%20and%20Response%20(MDR)%20Solutions%20(Key%20Features%2c%20Pros%2c%20and%20Cons).jpg)
Looking for the best Managed Detection and Response (MDR) solution for your company?
Finding a tool that suits the exact needs of your business can be confusing and drain your time. But don't worry, we've done all the hard work for you.
In this article, we've curated the five best MDR solutions along with their key features, pros, and cons. We've also suggested steps you should take to find the right solution for your company, as well as important features you need to look for in a Managed Detection and Response solution.
And we'll also reveal our #1 pick for the best overall MDR solution.
Let's get started.
What is Managed Detection and Response (MDR)?

Definition of MDR
Managed Detection and Response (MDR) is a comprehensive cybersecurity service that combines advanced threat detection, incident response, and remediation capabilities to protect organizations from emerging threats. MDR solutions are designed to detect and respond to security incidents in real-time, reducing the risk of cyber threats and improving an organization’s security posture. By leveraging cutting-edge technology and expert analysis, MDR services provide a proactive approach to identifying and mitigating potential security threats before they can cause significant damage.
Importance of MDR in Cybersecurity
In today’s rapidly evolving cybersecurity landscape, the importance of MDR cannot be overstated. As cyber threats become increasingly sophisticated, organizations need robust threat response capabilities to stay ahead of attackers. MDR services equip security teams with the necessary tools and expertise to detect and respond to advanced threats effectively. With access to security experts, threat intelligence, and scalable cloud security platforms, organizations can enhance their ability to manage security incidents and improve their overall security posture. By integrating MDR into their cybersecurity strategy, businesses can ensure they are well-prepared to handle the ever-changing threat landscape.
Managed Detection and Response Solutions Comparison
1. SilverSky
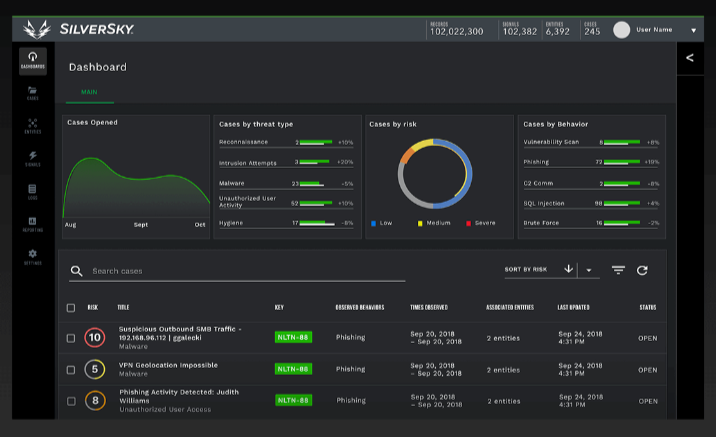
Key Features and Threat Intelligence
SilverSky is one of the world's leading Managed Detection and Response platforms for threat detection, response, and cyber protection. The technology is cutting-edge and everything is delivered on-demand as a worry-free, cost-effective, scalable managed service.
Silversky Pros
-
A comprehensive, centralized, and powerful platform of integrated security technologies
-
Enables businesses to get the most out of the technology they already have by ingesting information from 100s of cybersecurity products. It also ensures your tech is correctly configured to improve security gaps and make sure it does what it's supposed to do.
-
Monitoring of security operations carried out 24 hours a day, 7 days a week with the option of signing up for SIEM on-demand and SOC on-demand
-
A highly specialized team of +300 analysts and cybersecurity experts, for smooth and very efficient integration, so that there is no gap for attacks.
-
Low cost. Prices Start at only $11 per user with no upfront CAPEX costs and they can help your business transform its whole stack from CAPEX to OPEXThere is an extended trial period: 60 days free trial so that you can test the tool.
Silversky Cons
-
The number of tickets and notices can be intense, so if your company doesn't have a dedicated cybersecurity team, it runs the risk of missing important alerts.
-
Despite offering a consultancy service, SilverSky client companies that do not have a qualified team may find it difficult to determine what site or tool to use for each task.
2. Sophos

Key Features
Sophos Managed Detection and Response (MDR) is a solution that detects and responds to cyberattacks targeting your computers, servers, networks, cloud workloads, email accounts, and more.
Sophos Pros
-
The tool has a central dashboard where the user can see real-time alerts, reporting, and management.
-
Offers weekly and monthly reports provide insights into security investigations, cyber threats, and your security posture.
Sophos Cons
-
Although the system offers a complete view of the different risk levels of the systems used by the company, there is not enough information about low-risk threats, which can make the company susceptible to an attack if the problem is not resolved. User feedback suggests that there are problems when the system is updated, generating instabilities that can compromise monitoring.
-
There are also indications of failures when it comes to integration with other applications or machines, such as Apple computers, for example.
3. eSentire
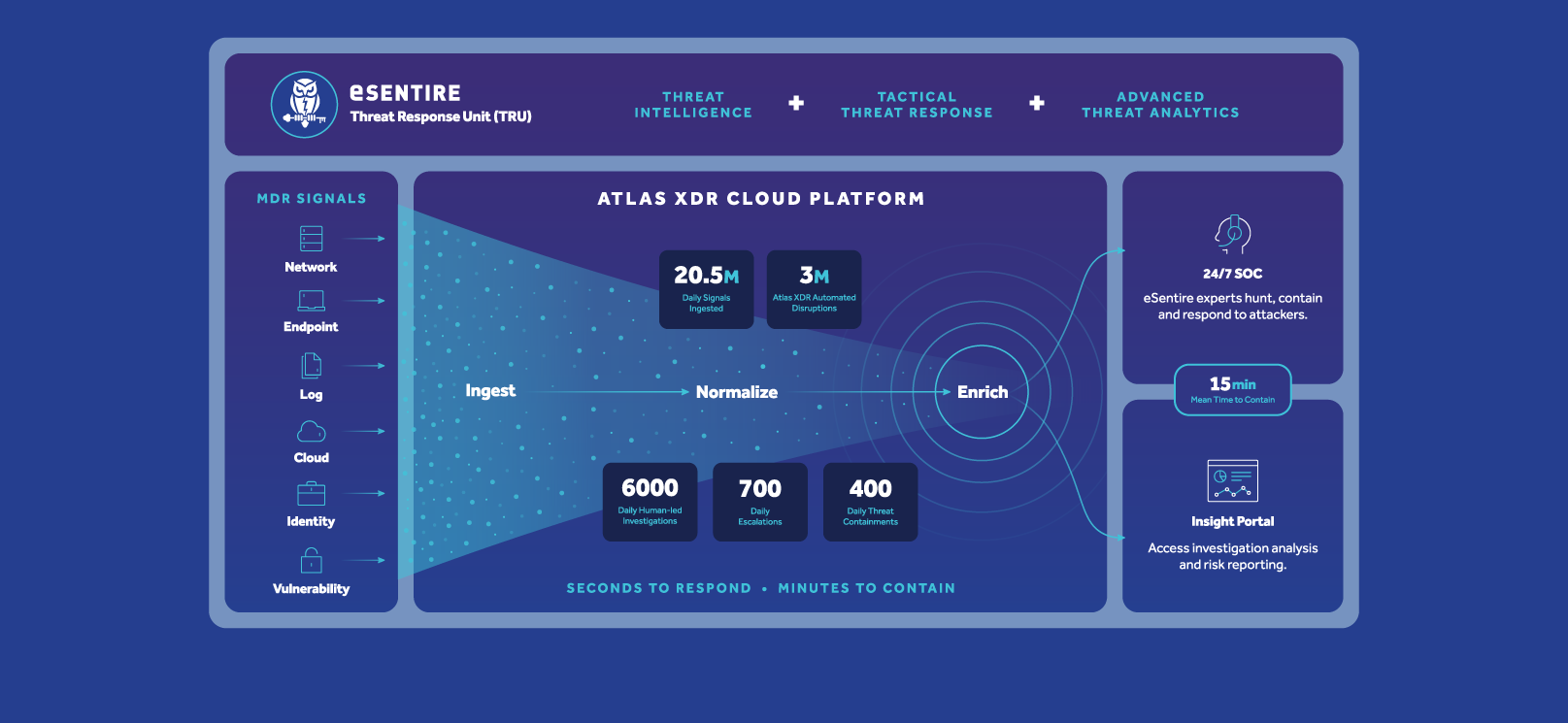
Key Features
The Canadian company protects the critical data and applications of 1500+ organizations in 80+ countries, representing 35 industries from known and unknown cyber threats.
eSentire Pros
-
The solution combines cutting-edge machine learning XDR technology, 24/7 Threat Hunting, and provides security operations leadership, eSentire mitigates business risk and enables security at scale.
-
They also provide Managed Risk, Managed Detection and Response, and Incident Response services.
eSentire Cons
-
User feedback suggests poor company advice after the setup, which leaves customers unassisted.
-
Lack of effective recommendations on actions that prevent companies from attacks through the identified gaps.
4. Arctic Wolf
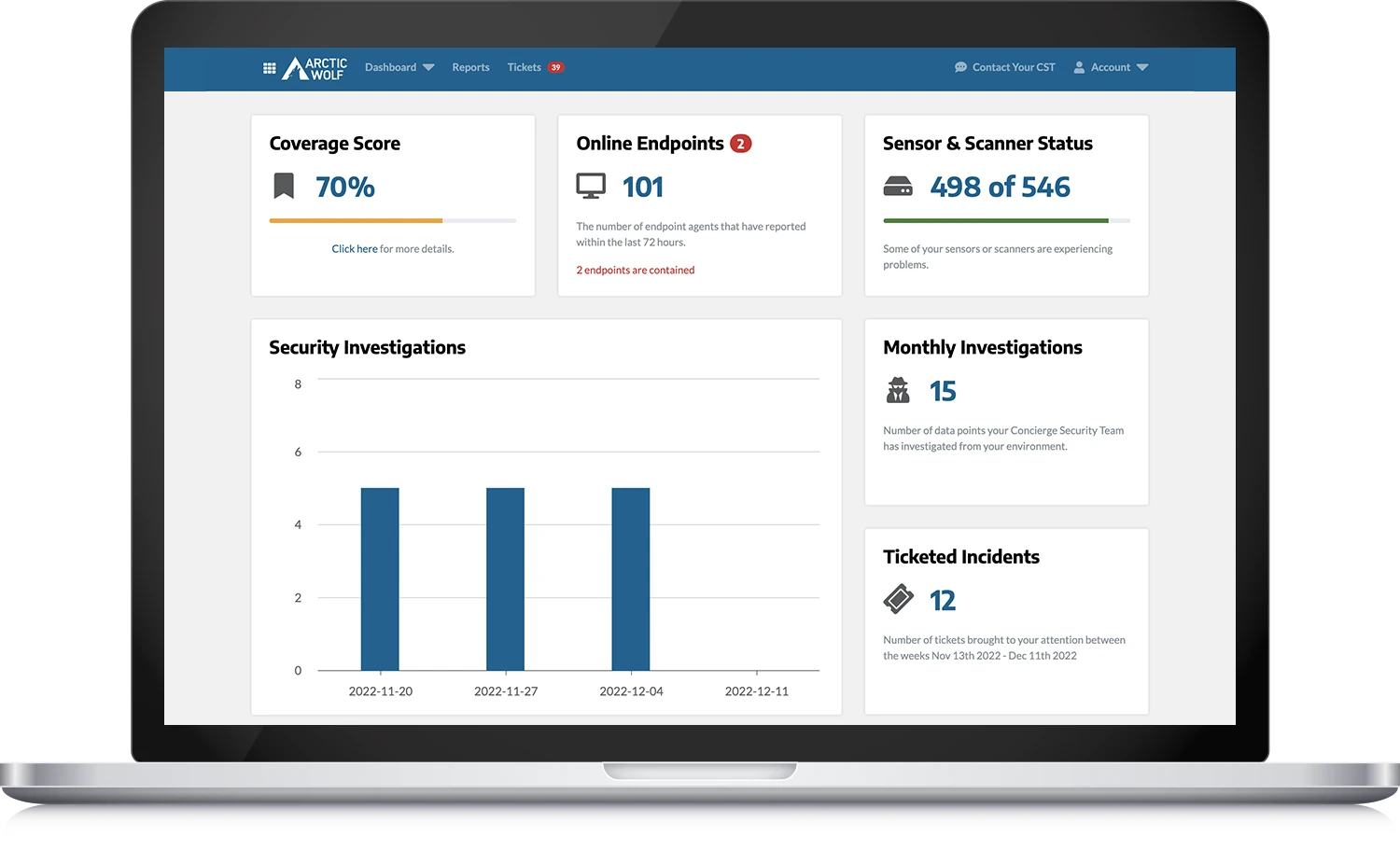
Key Features
Arctic Wolf platform was built on an open XDR architecture, combining a Concierge Security® Model to work as an extension of the company's security team to increase the security posture.
Artic Wolf Pros
-
Arctic Wolf Managed Detection and Response (MDR) solution provides 24×7 monitoring of the enterprise's networks, endpoints, and cloud environments, to help the companies detect, respond, and recover from modern cyber attacks.
-
Works with your existing technology stack to discover and profile assets and collect data and security event observations from multiple sources.
Artic Wolf Cons
-
Despite being a very complete solution, Arctic Wolf is lacking when it comes to alerts.
-
Customers have reported a large number of false positives.
-
The user interface isn't very intuitive.
-
The log search utility doesn't have enough documentation.
5. Rapid7
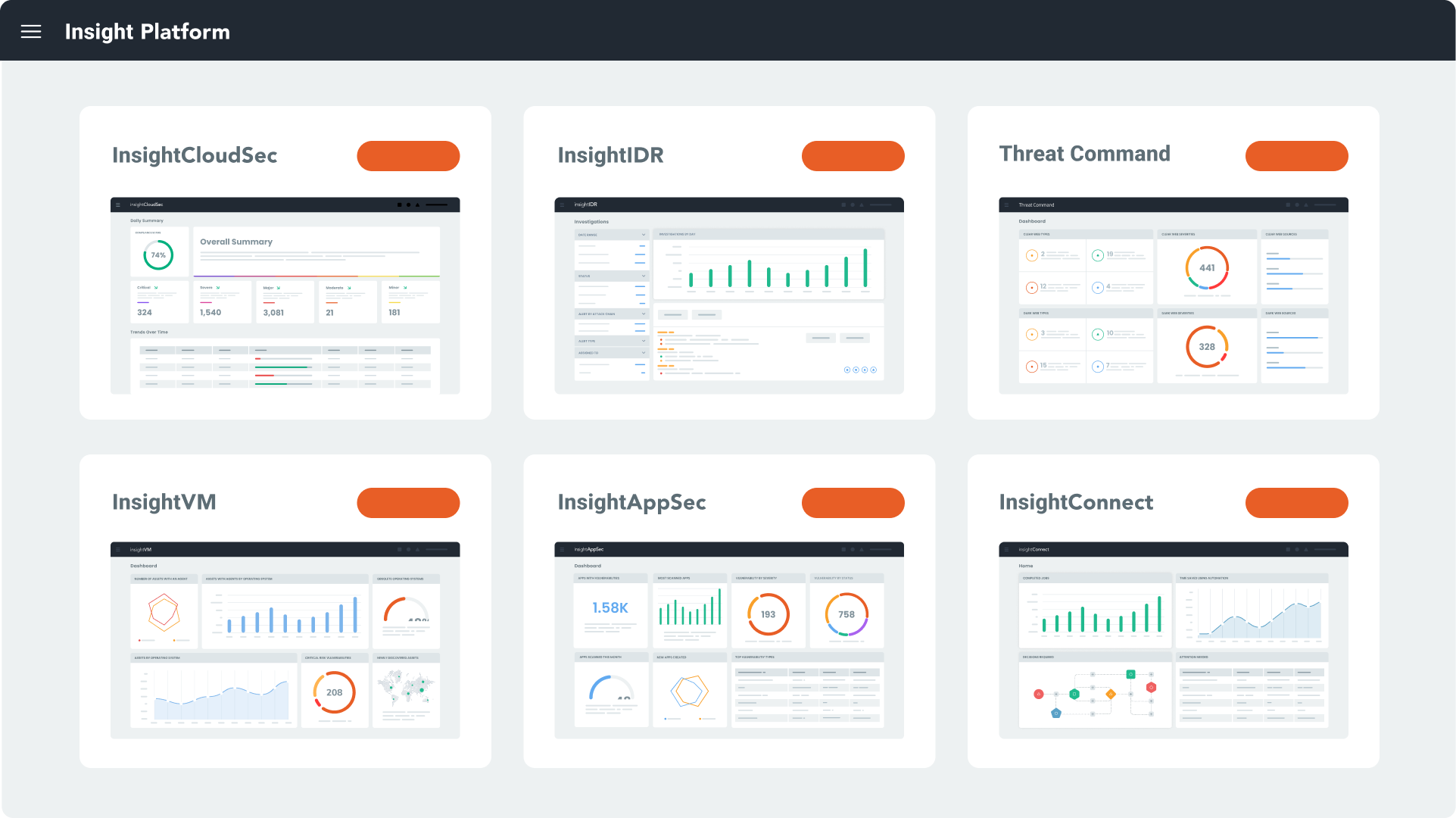
Key Features
Rapid7 is a platform that unites cloud risk management and threat detection to deliver results that secure businesses. MDR is one of the company's solutions.
Arctic Wolf Pros
Arctic Wolf’s MDR solution is a popular choice among organizations, offering several benefits, including:
-
Advanced threat detection and response capabilities that help detect advanced threats before they can cause significant damage.
-
Access to security experts and threat intelligence, providing organizations with the insights needed to stay ahead of emerging threats.
-
Scalable cloud security platforms that can grow with your organization, ensuring robust protection as your business expands.
-
Robust threat response capabilities that enable quick and effective remediation of security incidents.
-
Improved security posture through continuous monitoring and proactive threat hunting.
Arctic Wolf Cons
While Arctic Wolf’s MDR solution is a strong choice, there are some potential drawbacks to consider:
-
Higher cost compared to other MDR solutions, which may be a concern for budget-conscious organizations.
-
Limited customization options, which might not meet the specific needs of all businesses.
-
Dependence on Arctic Wolf’s security experts and threat intelligence, which could be a limitation if you prefer more control over your security operations.
Overall, Arctic Wolf’s MDR solution is a solid choice for organizations looking for advanced threat detection and response capabilities. However, it’s essential to weigh the pros and cons and consider the specific needs of your organization before making a decision.
Rapid7 Pros
-
Offers 24/7 monitoring and a partnership that helps deliver security strategy, shut down cyberattacks, solve skills gap challenges, and reduce risk.
-
The platform has expertly vetted detections that help companies spot critical threats early in the attack chain.
Rapid7 Cons
-
Some tools have not yet been automated, such as removing devices that have already been found or scanned. This generates unnecessary workload for the security team.
-
Customers report difficulties in implementing the platform and a gap until the start of the scan, which leaves the company vulnerable.
Is MDR The Right Solution For Your Company's Security Posture?
MDR platform providers act as your strategic partner, working together with your company's cybersecurity team. This type of service does not work for companies that want to completely outsource the security of their business. However, it is very efficient to avoid overloading operational tasks, energy in threat investigation, and excessive alerts.
In addition, MDR platforms need to be flexible and compatible with cybersecurity solutions already used by the company.
MDR is the ideal solution for companies that:
-
Already have cybersecurity solutions and want a platform that helps monitor and integrates all layers of business protection
-
Want a full solution that gives a complete view of the business, that helps them scale and automate repetitive tasks
-
Want a solution that, in addition to detecting threats, also has really effective responses
MDR is NOT the ideal solution for companies that:
-
Need specific support related to compliance and certifications
-
Don't have any existing cybersecurity solutions protecting your business right now, or are in the early stages of business development
-
Want to completely outsource the security of their business
For businesses who want a complete outsource solution for their cybersecurity, there are other excellent alternatives. Haven by Corvid Defense is a great example. It offers one package for a complete cybersecurity program with a low, monthly, per-user subscription with no capital expenses or required hiring of staff.
Haven bundles some of the most advanced solutions into a highly effective platform for your protection: endpoint security with SentinelOne, network protection with Palo Alto Networks, email security with Mimecast, phishing simulations with Symbol, and 24/7 monitoring with Corvid. To learn more, visit the full page.
How to Choose The Right MDR Vendor For Your Company: Focus on Threat Hunting
As mentioned earlier, there are hundreds of vendors offering MDR solutions. Each has different characteristics and solutions that meet specific sectors and needs. To make the right choice, follow these steps:
-
Carry out an efficient self-assessment to understand exactly your company's current needs in terms of cybersecurity
-
Search in-depth for available suppliers
-
Ask the right questions when interviewing prospective partners
-
Read testimonials and reviews from potential vendors' client companies
-
Chat with consultants
-
Make a trial to identify if the system is really compatible with the needs of the business
CyVent has performed this process with dozens of companies and our top recommendation is SilverSky. As one of the world's leading Managed Detection and Response platforms, Silversky offers a worry-free, cost-effective, scalable managed service, which is perfect for anyone looking to get the most out of the technology they already have.
Need Help Choosing and Implementing Your MDR?

CyVent can help. We have a team of experts who can help you understand your requirements and find you the best solution.
CyVent is a specialist in cybersecurity services and an advisory firm with over 100 years of combined experience and industry knowledge. Our experts will eliminate any confusion and guide you to the right cybersecurity solution for your unique system.
Click here to book a call and speak with one of our experts.

January is a month when many of us will be taking some time to plan for the year that is starting.
But, just for today, instead of looking at your forecasts for the next 12 months, I’d like you to take some time to think about what’s coming up over the next 10 years. Especially when it comes to technology.
The pace of change in tech has always been blistering. But according to many experts, we’re going to experience more technological progress in the next 10 years than we did in the previous 100.
Of course, when you’re running a business this can be an overwhelming prospect.
- Will you keep up?
- Will you choose the right tech for your company to flourish?
- Will it be damaging if you don’t adopt the right tech at the right time?
- Or could this be the opportunity of a lifetime?
The real challenge is knowing which changes will be most beneficial for your business.
This guide provides the lowdown on 8 technologies that are garnering the most interest from investors and tech thinkers right now.
These are the emerging technologies that you’re most likely to experience in your business at some stage – and they look set to change the landscape of the workplace over the coming decade.
As with anything in your business, preparation is key, so by learning about these technologies now you can be ready for the future.
8 Tech Trends to Watch
1. Process Automation
We spend a lot of time recommending ways our clients can automate many of their processes. It can help to create more streamlined systems, increase productivity, and simply make some jobs less tedious.
Over the next couple of years, around half of all existing work activities could be automated. That’s because next-level process automation is set to become the norm.
2. Connectivity
Digital connections are speeding up. We currently have 5G mobile connection (there’s already talk of 6G), and the IoT (Internet of Things). These have huge potential to unlock greater economic activity.
By 2025, 4.3 billion new devices, from cars to computers, will connect using mobile technology, and mobile will continue to dominate as the way we work and communicate.
In fact, it’s said that mobility, healthcare, manufacturing, and retail could increase global GDP by as much as $2 trillion by 2030. By then up to 80% of the world’s population could have 5G coverage.
5G and IoT are set to be some of the most-watched tech trends in the coming years.
3. Cloud and Edge Technology
It’s estimated that as many as 70% of companies are already incorporating cloud and edge technologies as a crucial part of their IT infrastructure. That figure is set to grow year on year.
Cloud computing is where the processing is done away from your device. Think of anything you log into through your browser. Your browser doesn’t process anything, it just shows you the information.
Edge computing is where the heavy processing is being done closer to where results are needed. For example, Netflix places servers closer to large groups of its subscribers as that speeds up video streaming times.
Has your business switched to cloud platforms as a way of running systems and storing data? If not, this may need to be one of your tech priorities for 2023.
Not only is cloud computing a good way to increase the speed and agility of your business, it reduces your hardware costs and also helps to improve your cyber security defenses, protecting you from malware, data theft, and other breaches.
By 2025, 75% of enterprise-generated data will be processed by edge or cloud computing.
4. Next-Gen Computing and Biometrics
Next-gen computing is a catch-all term that encompasses everything from quantum AI to fully autonomous vehicles. And though this might not be a primary concern for most businesses, it’s still something you should bear in mind as it’s definitely coming.
Your business may not be what we call ‘first wave industry’ (that’s things like finance, travel, and logistics) but you will, at some stage, adopt new tech like this.
And it’s worth remembering that this also includes things like biometrics. By 2025, 75% of companies plan to ditch traditional passwords, which means tools like facial recognition, retinal scanning, and signature identification will all become more commonplace. We’re already seeing these new, more advanced ways of logging into accounts with the advent of Passkeys which are slowly taking the reins from traditional passwords.
5. AI
We’ve already touched on AI – that’s Artificial Intelligence. It’s tech we’ve seen spreading everywhere over the past few years. Alexa and Siri are popular forms of AI that many of us already use daily.
We’re still very much in the early days of AI tech. It will become more advanced and be used to develop easier methods of training, and pattern recognition, which will help to further automate many of our business functions.
By 2024, AI generated speech will be behind 50% of our interaction with computers. Many businesses are still trying to work out how to incorporate AI most efficiently to make a difference to their bottom line.
But have no doubt, it’s tech that will gradually change everything.
6. The Future of Programming
Although you may not get directly involved with the programming of your apps and systems, the future of programming will have some form of impact on your business.
We’ll see programming written by AI-driven applications, making software creation faster and more powerful. It also means that existing software and coding processes can become standardized and automated across entire businesses.
Overall, it’s expected that there will be a 30 times reduction in the time it takes to create software and analytics.
7. Zero Trust Architecture
Last year there were 4,145 publicly disclosed data breaches that exposed more than 22 billion records. And it’s only looking to get worse. Realistically, we’re looking at a 5% increase, even despite the advances in cyber security.
That’s because cyber criminals are increasing their efforts all the time, developing ever more sophisticated methods of hijacking our data and sensitive information.
Zero trust architectures will become the standard approach to cyber security, especially for businesses. Not only can zero trust protect your business from more cyber crime, but it can also be a more cost-efficient form of security.
8. Clean Tech
As the world moves towards reduced emissions and a lower environmental impact, so too does technology and the businesses that use it.
Renewable energy, cleaner transport, and greater energy efficiency are all high on the future agenda. That means the costs of implementation will be lower and use will become more widespread.
It will be increasingly important for your business to stay environmentally aware as it will become a big deciding factor for prospects when choosing the companies they want to do business with. It will also be a big selling point when it comes time for you to grow your team. We’re already seeing candidates choosing companies that are more socially and environmentally conscious.
Advances in clean tech will mean that green energy can power the new technology you use, including high-powered computing.
By 2050, more than 75% of global energy will be produced by renewables.
And there we have it. The 8 top tech trends for the coming decade.
It may be daunting – but it’s also really exciting.
How many of these are already on your business agenda? And how much work do you think you’ll need to do to keep your business up to date?
We recommend that you start by thinking about your current tech and the ways it’s helping to make your business processes easier and faster.
Then think about the ways you could further use your tech to help your team become more productive (and happier and more engaged in what you do).
Our team keeps a constant eye on upcoming tech and how it can help businesses.
Would you like help to review your current cybersecurity setup and identify opportunities to reduce costs?
Get in touch – we’re here to help.
XDR vs EDR: What’s The Difference + 5 Strategies for Choosing The Best Solution Among MSSP, EDR, MDR or XDR
The alphabet soup of cybersecurity can be confusing. With so many cybersecurity acronyms, it can be a challenge to understand what a technology does and whether it's a good fit for your needs. Distinguishing between MSSP, EDR, MDR, and XDR is one of the most confusing areas, even for the most seasoned security leader.
In this post, we will help you understand each of the solutions better and provide criteria for deciding which is the best option for your company.
-
What are the main differences between MSSP, EDR, MDR, and XDR
-
The benefits and gaps
-
5 recommendations for choosing the right monitoring and response solution for your company

Managed Security Services Provider (MSSP)
A Managed Security Services Provider is a cyber security service that acts mainly in the prevention, monitoring, and detection of threats. A MSSP uses systems to monitor the company’s structure and alert whenever there is any potential risk.
Here are some tools and services that MSSPs usually include:
-
24/7 monitoring and management service
-
Assessment of security systems
-
Response to events
-
Exposure Assessments
These systems relieve internal teams and assume responsibility for continuous monitoring.
A survey by the consultancy IDC pointed out the top five reasons an organization turns to a Managed Security Service Provider (MSSP):
-
Need to protect against advanced security threats
-
Need for 24/7 support
-
Improve performance and availability
-
Access to new emerging security technologies
-
Need to maintain compliance regulations
However, while MSSP services are very good at detecting security alerts on a network, they often don’t include threat response. Therefore, it is important to understand the supplier’s offer well before closing the deal. There are different offers on the market, with different capabilities and competencies, which can even be customized to your company’s needs.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a specific solution for managing risks related to endpoints. With the rise of remote work, the number of endpoints has exploded, as have their complexity and specifications.
This has exponentially increased the number of cybersecurity threats. In fact, 51% of IT professionals consider their organizations ineffective at surfing threats because their endpoint security solutions are not effective at detecting advanced attacks.
In this way, traditional security platforms are often unable to meet the demand of some companies.
When integrating EDR solutions, it is crucial to assess existing security tools to ensure compatibility and comprehensive threat coverage.
The main functions of EDR include:
-
Continuously collect and analyze endpoint activity that can bring threats to the enterprise
-
Find patterns in endpoint behavior and monitor if there is a change
-
Offer complete and comprehensive information on all endpoint branches in a single dashboard
-
Notify the responsible team whenever there is a risk
-
When programmed to do so, respond automatically to isolate a detected threat
You can learn more about Endpoint Security in this blog.
However, the use of EDR is very specific and its use alone does not provide complete coverage for companies with complex network structures.
Managed Detection and Response (MDR)
Managed Detection and Response (MDR) platforms monitor a company's cybersecurity across its various network layers through a combination of technologies.
The main benefit of a MDR system is in the assessment of incidents and in the remote and fast response to contain the threat and reduce the risks for the company.
Different MDR systems usually respond to attacks using different approaches as well as technology. Some more advanced solutions have the potential to remediate attacks and still act in the gaps that allowed the attack, preventing future threats using the same vulnerability.
According to IDC, the core technologies and tools used in MDR services include advanced detection and analytics techniques such as:
-
Machine learning
-
Behavior analytics
-
Big data analytics
-
NetFlow analysis
-
Ongoing threat hunting to identify known and unknown threats
-
Automated scripts and playbooks
All of these techniques are important because they impact the quality of the notifications the security team will receive.
Extended Detection and Response (XDR)
Extended Detection and Response (XDR) is the most holistic approach of all solutions. Its purpose is to collect, correlate and analyze data in different security layers, for example, endpoints, emails, servers, and networks. This solution natively integrates multiple security products into a cohesive security operations system that unifies all licensed components.
XDR solutions often work alongside cloud security posture management (CSPM) tools to enhance threat detection and response across multiple cloud environments.
Although the performance of XDR systems is broad, their analytics are centralized and generally offer information in a single dashboard, which improves the user experience.
To make all the necessary correlations, XDR platforms make use of artificial intelligence, automation, and machine learning. As a result, they offer multiple alerts and warnings with context so that the security team can act intelligently on threats.
Based on data from the company itself and also from external systems, XDR analyzes alerts and provides the team with complete information and solutions to combat threats.
Key Differences Between EDR and XDR

EDR (Endpoint Detection and Response) and XDR (Extended Detection and Response) are two security solutions that have gained significant attention in recent years. While both solutions are designed to detect and respond to threats, there are key differences between them.
One of the primary differences between EDR and XDR is their scope of protection. EDR solutions focus on protecting endpoints such as laptops, desktops, and servers, whereas XDR solutions provide a more comprehensive approach to threat detection and response by integrating multiple security technologies. XDR solutions can collect and analyze data from various sources, including endpoints, networks, cloud applications, and email, to provide a more holistic view of an organization’s security posture.
Another key difference between EDR and XDR is their approach to threat detection. EDR solutions use advanced machine learning and behavioral analysis techniques to identify potential threats on endpoints, whereas XDR solutions use a combination of machine learning, behavioral analysis, and threat intelligence to detect threats across multiple environments.
In terms of response capabilities, both EDR and XDR solutions offer automated response capabilities, but XDR solutions provide more advanced automation and orchestration capabilities, allowing security teams to respond to threats more quickly and effectively.
Importance of EDR and XDR in Cybersecurity
EDR and XDR solutions are essential components of a modern cybersecurity strategy. With the increasing number of cyber threats and the sophistication of these threats, organizations need to have effective security solutions in place to detect and respond to threats quickly.
EDR solutions provide real-time visibility into endpoint activity, allowing security teams to quickly identify and respond to security incidents. EDR solutions also provide advanced threat detection and response capabilities, including behavioral analysis and machine learning, to detect and respond to threats that may have evaded traditional security solutions.
XDR solutions, on the other hand, provide a more comprehensive approach to threat detection and response by integrating multiple security technologies. XDR solutions can collect and analyze data from various sources, including endpoints, networks, cloud applications, and email, to provide a more holistic view of an organization’s security posture. XDR solutions also provide advanced automation and orchestration capabilities, allowing security teams to respond to threats more quickly and effectively.
MSSP and MDR: What’s The Difference?
MSSP (Managed Security Service Provider) and MDR (Managed Detection and Response) are two terms that are often used interchangeably, but they have distinct meanings.
MSSP refers to a service provider that offers a range of security services, including monitoring, incident response, and threat intelligence, to organizations. MSSPs typically provide a broad range of security services, including network security, endpoint security, and cloud security.
MDR, on the other hand, refers to a specific type of security service that focuses on detecting and responding to threats in real-time. MDR solutions typically use advanced machine learning and behavioral analysis techniques to identify potential threats and provide automated response capabilities to respond to threats quickly.
While MSSPs may offer MDR services as part of their broader range of security services, not all MSSPs offer MDR services. MDR solutions are typically designed to provide advanced threat detection and response capabilities, whereas MSSPs may offer a broader range of security services.
In summary, MSSP refers to a service provider that offers a range of security services, whereas MDR refers to a specific type of security service that focuses on detecting and responding to threats in real-time.
5 Recommendations For Choosing The Right Solution For Your Company

Faced with so many options, how do you choose the right solution for your company? When evaluating new solutions, consider how they will integrate with your existing security tools to provide a cohesive security posture. Here are 5 key considerations that must be taken into account:
1. Cybersecurity Budget
Company budget is fundamental to understanding how much can be invested in cybersecurity. It is important to remember that the most effective solutions are not necessarily the most expensive. There are great value end-to-end solutions like SilverSky and Haven.
2. Your Current Tools And Technology Stack
When procuring a new solution, it is important to consider the tools and technologies your company already has. The company needs to have complete clarity of what its current systems are and are not capable of doing, in order to identify the gaps it needs to fill. The new solution must be compatible, and able to integrate and work together with the systems that the company already uses.
3. Request a Demo
Before purchasing a new solution, give your end users a demo so they can experience the platform firsthand. Most vendors provide this and it must be done so that your team is sure that the solution will be simple to use and implement.
4. Read Testimonials From Other Companies
Even if you don't have a direct indication of the quality of a cybersecurity platform, a great way to do this is to check what customers say about its usability. Read testimonials, evaluate case studies, and, if you can, talk to companies that already use the platform. Consider companies that face similar challenges to yours and use that as a basis for making your decision.
5. Consider Your Future Business Plans
Purchasing a tool often means signing a long-term commitment with a supplier. The choice of a provider must also take into account the company's growth plans. SaaS cybersecurity solutions allow you to increase your requirements as you grow.
There are several options for managed detection and response cybersecurity solutions. Before purchasing the service, the company needs to understand the differences between each of them and what their needs are to protect the company.
This article has highlighted the main features and differences between MSSP, MDR, EDR, and XDR solutions.
If you're unsure which is the ideal solution to protect your business against the complex threats that exist today, seek specialized help. CyVent experts are on hand to assist in the diagnosis, strategy, and implementation of a cybersecurity solution for your business.
If you want more information, book a discovery call at https://www.cyvent.com/assess-company-cyber-threats/-0
The Ultimate Pentesting Guide: The #1 Way To Expose Your Cybersecurity Weaknesses
You invest in cybersecurity tools, train your employees, and establish habits that protect your business data from hackers. But is that enough? Will your company survive when it faces a cyberattack? The penetration test has the answer.
The penetration test, also known as Pentest, is a training method that simulates an invasion of the company's systems. It ensures that the company covers all gaps before it's too late.
According to the 2020 Penetration Testing Report, only 3% of companies believe that penetration testing is not important to their security posture.
In this article, we'll walk you through everything you need to know when performing pen testing, including:
-
Why Having a Pentest Is Important For Your Company?
-
5 Excellent Reasons For You To Schedule a Pen Test For Your Company Right Now
-
The 4 Most Common Types of Pen testing
-
Who Should Run The Penetration Test?
-
What Is The Difference Between a Penetration Test And a Vulnerability Scan?
-
What Happens After the Pentest?
What is Penetration Testing?

Penetration testing, often referred to as pen testing or ethical hacking, is a proactive approach to cybersecurity. It involves simulating cyber attacks on a computer system, network, or web application to evaluate its security. The primary goal of penetration testing is to uncover security weaknesses and vulnerabilities that could be exploited by malicious actors to gain unauthorized access to sensitive data or disrupt system functionality. By identifying these vulnerabilities, organizations can strengthen their security posture and prevent potential breaches before they occur.
Why Having a Pentest Is Important For Your Company?
The National Institute of Standards and Technology (NIST) defines the Penetration Test as: “A method of testing where testers target individual binary components or the application as a whole to determine whether intra or intercomponent vulnerabilities can be exploited to compromise the application, its data, or its environmental resources.”
In simple terms, the pentest highlights the company’s cybersecurity weaknesses and uncovers security vulnerabilities that need to be corrected.
According to The State of Pen testing 2022, these are the 5 most frequently discovered vulnerability categories found in 2021: 1. Server Security Misconfigurations: 38% 2. Cross-Site Scripting (XSS): 13% 3. Broken Access Control: 11% 4. Sensitive Data Exposure: 10% 5. Authentication and Sessions: 8%
In this way, pen testing allows the security team and also the IT team to have clarity on the weaknesses of the infrastructure. As a result, professionals can act quickly to address vulnerabilities, according to priorities.
In addition to helping with the structural issue, this type of method also allows testing the company’s ability to inform the team of the existence of a threat and also to score the team’s response to the incident.
5 Excellent Reasons For You To Schedule a Pen Test For Your Company Right Now
1. Exposes Your Company's System And Infrastructure Vulnerabilities
Through penetration testing, hackers identify vulnerabilities in the infrastructure and also in the system settings. A penetration tester simulates cyber attacks to identify these vulnerabilities and assess the security measures in place. This includes not only technical issues but also user habits, which could be creating breaches for intruders to enter.
2. Test The Effectiveness Of Your Cybersecurity Features
Often, the company is confident that its cybersecurity investments are enough. However, this is not always true. The penetration test evaluates security barriers and acts as a black hat hacker would.
Plus, it helps you test whether your Incident Response Plan measures up to combat a real threat.
In this blog post, we have gathered 6 important elements to check before finalizing your Incident Response Plan.
3. Helps You Build Really Effective Employee Training
Pentest puts your company's employees in a risky situation. Pentest assesses employee response to social engineering, including phishing and business email compromise attacks.
According to the Cost of a Data Breach Report 2022, the most common initial attack vectors were compromised credentials at 19% of breaches, followed by phishing at 16% of breaches. The average cost of data breach with a phishing initial attack vector is USD 4.91 million. Testing your employees' responses helps directors identify which behaviors should be improved and which processes need to be polished for the result to be positive.
Going through this experience also sensitizes employees, improving engagement in training.
4. Helps Your Company Improve Compliance And Earn Certifications
Cybersecurity is increasingly an important criterion for closing deals. The positive result of a penetration test can be part of your compliance program and also the achievement of important certifications, such as the ISO 27001 standard and the PCI regulations.
5. Offers An Action Plan To Improve Your Cybersecurity
After carrying out a penetration test, the company receives a complete report with all the vulnerabilities found, all the errors that must be corrected, and the elements that can be improved, in the hardware and the software. All this is accompanied by an in-depth and specialized analysis, with recommendations that will effectively improve the company's barriers against cyberattacks.
A consistent pentest considers ALL vulnerabilities. As Window Snyder states, “One single vulnerability is all an attacker needs”.
The Penetration Testing Process
The penetration testing process is methodical and involves several critical phases:
-
Reconnaissance: This initial phase involves gathering as much information as possible about the target system. Penetration testers collect data such as IP addresses, domain names, and network topology to understand the target’s structure and potential entry points.
-
Scanning: In this phase, testers use tools like Nmap and Nessus to identify open ports, services, and vulnerabilities within the target system. This step helps in mapping out the attack surface.
-
Gaining Access: Here, testers exploit the identified vulnerabilities to gain unauthorized access to the target system. This phase demonstrates how an attacker could breach the system and what data or functionalities they could compromise.
-
Maintaining Access: Once access is gained, testers attempt to maintain their presence within the system to gather more information or escalate their privileges. This phase simulates how attackers might persist in a compromised environment.
-
Covering Tracks: Finally, testers cover their tracks to avoid detection. This step is crucial for understanding how attackers might hide their activities and evade security measures.
The 4 Most Common Types of Pen testing

There are different types of penetration tests that can be performed. Below, we list 4 main ones:
1. External Pen Test
In this type of test, ethical hackers, together with an experienced cybersecurity team, are hired by the company to perform the penetration test focusing on the website and network servers that are external to the company.
2. Internal Pen Test
This test involves exercises that start from the company's internal network. It starts from the access of an internal person to the company, such as an employee, to simulate an internal threat.
3. Blind Pen Test Or Closed-Box Pen Test
In this test, the hacker performing the exercise does not receive any information about the company other than his name. To carry out the invasion, the professional seeks data from open sources. However, the company is aware of the pen testing.
4. Double-Blind Pen Test
This test is a more advanced version of the Blind Pen Test. In this case, in addition to the hacker not having any information about the organization, almost no one in the company knows that the test is being carried out. In this way, the exercise really assesses the internal capabilities to respond to a threat.
Penetration Testing Tools and Techniques

Penetration testers employ a variety of tools and techniques to simulate cyber attacks effectively. Some of the most commonly used tools include:
-
Nmap: A powerful network scanning tool that helps identify open ports and services on a target system.
-
Metasploit: A comprehensive penetration testing framework that allows testers to exploit vulnerabilities and gain access to target systems.
-
Burp Suite: A versatile web application security testing tool used to identify vulnerabilities such as SQL injection and cross-site scripting (XSS) in web applications.
-
Social Engineering Toolkit (SET): A tool designed to simulate social engineering attacks, including phishing and spear phishing, to test human vulnerabilities.
Best Practices for Penetration Testing
To ensure penetration testing is effective and yields valuable insights, organizations should adhere to best practices, including:
-
Conducting Regular Penetration Tests: Regular testing helps identify and address vulnerabilities before they can be exploited by attackers.
-
Using a Variety of Testing Methods: Combining manual and automated testing methods ensures a comprehensive assessment of all potential vulnerabilities.
-
Testing for Social Engineering: Including social engineering penetration testing helps identify weaknesses in human behavior that could be exploited by attackers.
-
Providing Training and Awareness: Educating employees about cybersecurity threats and best practices helps prevent social engineering attacks and improves the overall security posture.
Penetration Testing for Cloud and Application Security

Penetration testing is crucial for ensuring the security of cloud-based systems and applications. This specialized form of testing involves simulating cyber attacks to identify vulnerabilities and weaknesses specific to cloud environments and applications. Key techniques include:
-
Cloud Security Testing: Assessing cloud-based systems and applications for vulnerabilities that could be exploited by attackers.
-
Web Application Security Testing: Evaluating web applications for common vulnerabilities such as SQL injection and cross-site scripting (XSS).
-
API Security Testing: Testing APIs for weaknesses in authentication and authorization mechanisms that could be exploited.
-
Container Security Testing: Assessing containerized applications, such as those using Docker and Kubernetes, for vulnerabilities that could compromise the container environment.
By following these practices and leveraging specialized tools and techniques, organizations can significantly enhance their cybersecurity defenses and protect their sensitive data from potential breaches.
Who Should Run The Penetration Test?
When the company has an internal cybersecurity team, it is common for the internal penetration tester to carry out periodic tests to identify the effectiveness of security policies. However, the ideal way to carry out this procedure is by an external team, which does not know the internal processes of the company.
Find out more about the Penetration Test here
The team is usually composed of “ethical hackers”. Experienced professionals, who think like cybercriminals and are able to look for blind spots in company cybersecurity.
Despite its importance, a recent survey revealed that 88% of businesses review security risks on their own, rather than using a vulnerability management solution.
What Is The Difference Between a Penetration Test And a Vulnerability Scan?
Vulnerability scanning is widely used to verify the security level of an institution. It scans your systems and IT infrastructure thoroughly, identifying any known security vulnerabilities and reporting their level of criticality.
Pentest does a similar job. However, through a team of ethical hackers, it is possible to put these vulnerabilities to the test and identify how far a hacker can go within the current context.
These two features must be used together to ensure that the company has good cybersecurity backing.
How Often Should Penetration Tests Be Performed?

As seen above, vulnerability scanning is a complementary test to pen testing. It has the advantage that it can be automated, which allows it to be carried out more frequently. Scanning can be done daily or weekly, for example.
The penetration test, on the other hand, needs more preparation time, as it involves hiring a specialized team.
There is no ideal frequency for performing the penetration test. This will depend on the characteristics of the company, its size, and its available budget. The ideal is to get the support of a specialized security consultant, who will assess the business and identify the ideal frequency.
In addition to periodic tests, it is recommended to carry out a new process every time there is a considerable change in the company. For example change of physical address, hiring new employees, software change, relevant software, and infrastructure upgrades.
Regulations and certifications related to the company's sector must also be taken into account. Some organizations must follow specific standards for performing security tests.
An interesting aspect of the penetration test is that it doesn't have to be done on a large scale. It is possible to perform focused tests more frequently, in areas that the company deems to be more critical. While broad and comprehensive testing is performed annually, testing focused on priority areas can be done every quarter, for example.
Retaking the test is also important. After testing and fixing the most critical vulnerabilities, it is common to carry out a new exercise to ensure that the changes were sufficient. This test is usually more agile and quick. There are tools that help in its conduct, identifying the most critical points pointed out in the previous report.
What Happens After the Pentest?
What happens after the penetration test is more important than the test itself. The professionals involved in the test prepare a report with all the findings and also an action plan that includes the next priority steps. The company needs to take the findings and recommendations seriously.
The security and development team need to work together to fix the vulnerabilities.
The State of Pen testing 2022 reveals that the median number of days teams needed to fix vulnerabilities is 14, but there are situations where they take 31 days or longer. However, the study also reveals that teams are struggling to fix and prevent the same vulnerabilities for at least the past 5 years in a row.
The most critical changes should be prioritized, but low-risk vulnerabilities should not be overlooked.
Employee training should also be updated according to perceived vulnerabilities in relation to the human risk factor.
Conclusion
Performing penetration tests within the company offers fundamental self-knowledge for the organization. With reporting data, security and development professionals can identify the highest-priority vulnerabilities.
In this article, we have highlighted the importance of pen testing, the 4 main types of penetration tests, who should perform the exercise, the difference between pen testing and vulnerability scan and also what should be done after the penetration test.
Need help testing your cybersecurity?
Do you need help running a penetration test in your company? CyVent and 24by7 offer Penetration Testing Services.
Our experts are on hand to help you with:
-
In-depth penetration testing, including black box, gray box, and white box tests
-
Verification of overall security posture, including assessments of your network, wireless network, and cloud environment
-
Assessment of employee response to social engineering, including phishing and business email compromise attacks
-
Identification of potential vulnerabilities to ensure compliance and reduce operational and reputational risks
If you want more information, book a call on https://www.cyvent.com/assess-company-cyber-threats/
6 Steps To Creating An Outstanding Cybersecurity Incident Response Plan [Free Templates]
Incident Response Plan is the #1 defense strategy to prevent a major crisis when it comes to cybersecurity. After all, as Jamie Ward famously says, “Cyberattack is not a matter of ‘if’, but ‘when’”.
In this article, we'll walk you through the critical elements for the security team when creating a new plan or updating existing plans. Including:
- Why having a Cybersecurity Incident Response Plan is important
- 4 Examples of the best Cybersecurity Incident Response Plans
- The 6 Key 'Must Haves' in every Incident Response Plan
- The post-incident response plan
Why Having A Cybersecurity Incident Response Plan Is Important
The National Institute of Standards and Technology (NIST) defines Cybersecurity Incident Response Plan (CIRP) as: “The documentation of a predetermined set of instructions or procedures to detect, respond to, and limit consequences of a malicious cyber attack against an organization’s information system(s).”
Having a CIRP cannot be underestimated by companies. Research shows that companies that prepare to deal with the effects of a cyberattack efficiently have a considerably lower average loss.
According to The Cost of Data Breach Report 2022, the average cost of a breach for businesses with incident response (IR) capabilities is 58% lower than those without IR capabilities. Breaches at organizations with IR capabilities cost an average of $3.26 million in 2026, compared to $5.92 million from organizations with no IR capabilities.
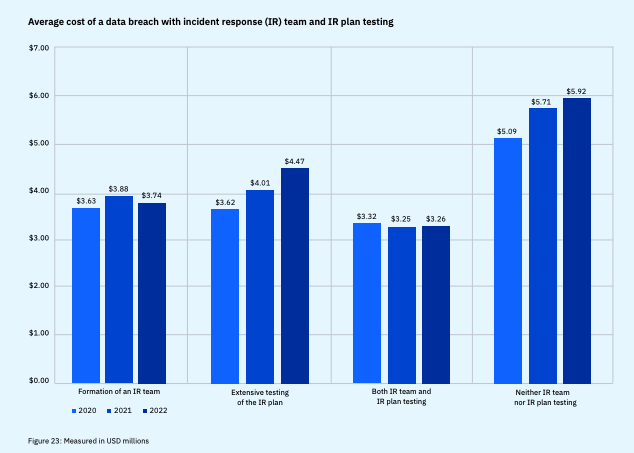
So why do businesses with incident response plans have lower breach costs? Having a complete and up-to-date CIRP implies constantly passing on information to employees and offering training. This helps to create an organizational culture that favors the recognition and prevention of cyber threats.
Another aspect is that by directing efforts to prevent attacks, it is possible to have more clarity on the cybersecurity gaps that are being left. That means you can correct them before they are found by criminals. All this allows an incident to be corrected much more quickly and efficiently.
However, not all companies have a plan. According to a survey by shred-it, 63% of C-level executives and 67% of small businesses in the U.S. do not have an incident response plan.
Another problem is that many plans are not done completely and consistently. For example, many security leads just focus on the most critical incidents. Yet, any fragility or risk to an endpoint must be defended vigorously to prevent a loophole allowing criminals from accessing valuable information.
A consistent cybersecurity plan considers ALL vulnerabilities. As Window Snyder states, “One single vulnerability is all an attacker needs”.

4 Examples of The Best Incident Response Plans
Here are four of the best examples we’ve pulled together that you can use as a blueprint to guide your planning for possible attacks.
Michigan Government Incident Response Plan
Computer Security Incident Handling Guide - NIST
Incident Response and Management: NASA Information Security Incident Management
Cyber Incident Response Plan - Government of Victoria, Australia
The 6 Key 'Must Haves' In Every Incident Response Plan
When it comes to creating a robust cybersecurity incident response plan, there are six key aspects that need to be included:
1. Prioritize Incident Levels
Prioritizing the incident level of an attack is critical to quickly identify the risk of the attack. This involves understanding which systems are critical to the functioning of your business and understanding the different types of user risk interactions. As seen in the Human Factor Report 2022 diagram below.
2. Complete Visibility of All Your Company's Systems And Resources
Clarity is a key aspect of the incident response plan. Knowing all the assets and resources that the company has is important when defending them. In addition, having complete visibility into the company's up-to-date data is critical to knowing where to act and in what way. Therefore, access to detailed and real-time data on the functioning of the company's systems is essential. With this, an attack can be identified more quickly.
3. Define Incident Response Plan Responsibilities
Establish those responsible for each stage of the plan, providing their level of authority and the list of responsibilities. This step is important because it allows people to act faster.
Create a full-time team to handle incident response or train staff to be on call. Professionals must have sufficient authority and responsibility to make the necessary decisions quickly.
Quick response to incidents is crucial on holidays and weekends because there is often a reduction in company protection. We know that Ramsonware is detonated every day of the week, as seen in the data below from RiskRecon.
4. Security Partners
Asking for help is no shame. On the contrary. Having reliable suppliers can prevent huge damage to the company. Therefore, it is important that these partners are mapped and that the team responsible for cybersecurity has easy access to the list. These contacts may include government security officials, privacy regulatory authorities, audit committees, press offices, etc.
5. Easy Access to CIRP
Another key point is to ensure that all employees and people relevant to the company have access to the CIRP. There's no point in putting together an incredible and complete plan if no one knows it exists. It is also important to consider a backup so that the document is accessible even if the internal servers are compromised.
6. Constant Training
Employees must be trained and have clarity on the steps that must be followed in the event of a threat, as well as their responsibility in attack situations. Training is best delivered little and often, just as software and systems must be updated periodically to stay ahead of the latest threats.
The Importance of Simulated Attacks
One of the best ways to equip employees with the skills to respond to attacks is with simulated attacks. They are designed to test everything that was established in the plan and delivered in training.
One of the most effective training programs is the Red Team Exercises, which simulate the conditions of an attack to identify vulnerabilities in your company's system. This type of exercise is critical to testing an incident response plan before it is done by a real hacker.

Why You Need A Post-incident Response Plan
A post-incident response plan helps the company to be more protected from the next attack.
This involves documenting everything to form history and feed a repository that will help the company to be more prepared for future attacks. Including the actions that were taken, the protocols that were made, and the measures that effectively eradicated the incident.
There are several CIRP frameworks. The National Institute of Standards and Technology (NIST) is one of the most recognized and includes four steps:
- Preparation
- Detection & Analysis
- Containment Eradication & Recovery
- Post-Incident Activity
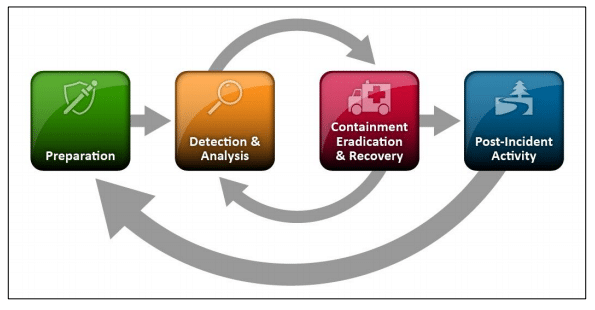
The unique part about the NIST approach is it foresees a non-linear action. That is, the plan must always be revisited and updated according to new information, new threats, and new skills of the team.
Likewise, after an attack, the plan must be updated. This can be taken a stage further by exchanging incident breach experiences with other companies can help your organization to be more prepared.
Here are some questions that can help when it comes to updating the plan after an attack:
- What attack was carried out and at what exact moment did it take place?
- What was the cybercriminal's entry point?
- Who perceived the threat and at what time?
- What was the first act after the incident was detected?
- How was the team informed about the problem? What was the team's reaction?
- What steps were taken to combat the problem? Who led this process?
- What were the positives and negatives of the responsible team approach? What is the lesson in preparing for the next incident?
- How can we prepare ourselves not to leave gaps and not suffer from this type of vulnerability in the future?
- Can any tool or system help us detect this type of vulnerability and respond more quickly to this type of attack in the future?
- What aspects, learned from this incident, can we include in staff training so that staff is better prepared?
Conclusion
Research shows that having a Cybersecurity Incident Response Plan (CIRP) significantly reduces the cost of a cyberattack on a company. However, many companies don’t have a robust plan in place or fail to update them consistently. To be effective, a CIRP must be constantly revisited and updated.
In this article, we have highlighted the importance of having an incident response plan, best practice examples of incident response plans, the 6 key 'must haves' in every Incident Response Plan, and why you need a post-incident response plan.
Need help creating your CIRP?
Need help creating a cybersecurity incident response plan? CyVent has access to the leading IR solutions. We rigorously curate our approved partners and monitor all stages of implementation. We also carry out training and tests that will raise the level of your company's response and make it more prepared to face threats.
CyVent experts are on hand to help you create the plan, train your employees, and choose the right tools to protect your business.
If you want more information, book a call on https://www.cyvent.com/assess-company-cyber-threats/
According to the Computer Security Resource Center definition, Phishing is “a technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a website, in which the perpetrator masquerades as a legitimate business or reputable person”. This scam is increasingly common and has devastating consequences for companies.
According to IBM's Cost of a Data Breach Report 2021, Phishing was the second costliest average total cost of the 10 initial attack vectors in the study, at $4.65 million. Furthermore, phishing was the second most frequent initial attack vector, being the gateway to 17% of threats.
The different types of Phishing:
There are different types of phishing. Below, we list some of the most common:
Email Phishing: attacks carried out through messages via email, using fake domains, which imitate those of real companies. It can trick the victim into clicking on a malicious website, making a suspicious download, or tricking them into sending information.
Spear Phishing: While Email Phishing is sent in bulk, for many people, Spear Phishing is personalized, through an email with personal information from the person receiving the message. With this, the chances of the victim falling for the scam is much greater.
Whaling: This Phishing scam targets the “big fish”, meaning the company's top executives. These people usually have a lot of information available on the internet. With dedication and study, scammers manage to mount a very believable bait, which increases the chances of the victim falling for the scam. This type of attack is worrying, as CEOs and C-Levels have access to especially sensitive company information.
Voice Phishing: Voice simulation programs are getting more and more sophisticated. Through this type of resource, scammers are able to simulate voice messages and even phone calls, posing as banking institutions, for example, to collect information or practice scams.
Smishing: This scam involves fake SMS messages. Scammers usually use information from leaks, or information collected from research on social networks, to make the scam seem more real.
These Phishing messages typically follow patterns such as:
- Sense of urgency
- Presence of writing errors
- Unusual requests such as payments or credential information
- Use of non-standard company logos
Given the importance of this threat, here are some strategies that can help your company protect itself from scams:
Tips to protect your business from Phishing Scams:
Qualified and constant training of employees
Keeping employees trained and on the lookout is critical to ensuring a functional end-to-end cybersecurity strategy. Attacks by criminals are increasingly sophisticated, ranging from viruses disguised as attachments to well-rehearsed phone calls.
According to Google's Transparency Report, 46,000 new phishing websites were created every week in 2020.
Employees need to know the dangers, the risks of attacks, and the correct procedures for acting in a phishing situation.
This training can be done by the internal cybersecurity and technology team or delivered automatically by a partner company through short 2-3 minute videos.
Controlled tests
Sending controlled tests allows you to identify the extent to which your company is susceptible to attacks. In addition, fictitious attacks give clues to where the biggest vulnerabilities are and which aspects of cybersecurity the company should strengthen.
A good password strategy
Passwords are a particularly sensitive topic when it comes to phishing. Without the correct management of passwords, with single access, the hacker can have control over several logins. Thus, in addition to training your employees to create strong passwords, it is important to raise awareness about the use of unique passwords for each access, reducing damage in the event of an attack.
Install good email protection solutions
The corporation can invest in efficient solutions to stop suspicious messages and requests through its inbound channels. These malicious emails are blocked and tested by the tools, preventing the scam from reaching the recipient.
CyVent proudly offers Haven, a managed protection, detection, and response solution as a service made for businesses of all sizes, providing enterprise-class security protection, along with controls, management, and monitoring options, with an excellent protection program for your endpoints, your network and your emails.
Use the principle of least privilege
Restricting server access is also a good alternative to protect information. Employees should have access to basic servers, accessing servers with more important information only when necessary. That way, in case of phishing, the threats are found.
The problems your company faces are unique. So your answer should be too. With CyVent you have expert support, cutting-edge software, and access to rigorously selected solutions with 24/7 monitoring.
Book a call: www.cyvent.com/contact-us
Artificial Intelligence and Information Security: Fact vs Fiction
Machine learning, deep learning, generative adversarial networks and other AI technologies have burst onto the cybersecurity scene over the last year. Software vendors and MSSPs are scrambling to bring their particular flavor of AI cyber security to market and claim their stake as industry leaders.
While AI has quickly become table stakes for an effective security posture, some of it can also seem to be overhyped in some respects. In this post, we’ll aim to cut through the superlatives and provide a few thoughts on the role of artificial intelligence in cyber security.
Artificial Intelligence in Cyber Security Does Not Replace Traditional Tools
By claiming that AI will replace traditional tools while lowering labor costs and probably making coffee at the same time, some advertising has put AI on a pedestal that it may not have achieved yet.
Here are some things that AI cyber security definitely will not replace. Security teams will still need to keep around:
- Employee training and a security-sensitive culture
- Smart policies and processes
- Qualified architects, managers, engineers, and analysts
- Rock-solid, layered infrastructure with effective controls around it
If you find yourself saying, “Wait, that’s 95% of my security program,” you’re right. Artificial intelligence in cyber security is a complement to a well-run cyber framework, not a replacement for it.
Must-Ask Questions When Evaluating AI Cyber Security Tools
We all have seen that technology can be promoted with grand promises backed by sometimes disappointing results. To avoid a dud in your AI implementation, you may want to sit down with your security team and your vendor rep to go over a few questions:
- How do your AI algorithms actually work? How mature is the technology? What are its blind spots?
- How well does it avoid false positives and false negatives?
- How do you measure the incremental benefits and the expected ROI?
- How will it protect us from insider threats?
- What’s your definition of ‘real-time’?
- Which attack vectors, file type, operating systems do you cover?
- How frequently does it need to be updated?
- How does it handle APT’s, zero-days and zero-hours?
- What outside support are we going to need to implement and maintain this?
- How much additional training will we need to use this effectively?
- Does it produce usable reports that actually mean something?
- What results have your other clients seen from it?
- Does it outperform what I already have, or will it be just another software bloating up my network?
Pitfalls to Avoid When Implementing an AI Cyber Security Solution
Adding software to your organization’s toolkit is rarely a trivial matter, and even less so when you’re dealing with AI. Here are some potential mistakes when deploying an AI cyber security tool:
- Expecting a “set-and-forget” solution that will replace the whole security program: See the first section of this post.
- Thinking that an in-house developed solution will be best-in-show without exploring other available options.
- Expecting that the AI tool won’t require any customization or integration.
- And possibly the most delicate one: Thinking it’ll all work out on automatic pilot without specialized AI expertise on your team or assistance from AI safety experts.
The fact of the matter is that it is no longer viable to delay implementation of robust AI cyber security tools. Bad actors have already started using AI.
A talented cybersecurity team and company-wide awareness trainings go a long way. Artificial intelligence in cyber security simply brings a needed support structure that can assist your teams to prevent attacks and accelerate mitigation if needed. As businesses undergo the digital transformation, it is imperative they also leverage new developments in cyber capabilities and include them in their thinking from the very beginning of their process. Cyber security cannot be an after-thought.
CyVent is a Certified Partner of global leaders in augmented intelligence applied to cybersecurity. Our cutting edge, AI-driven solutions help organizations transition from the classic remediation approach to security to a more pre-emptive posture, which ultimately increases prevention, decreases times-to-resolution and automates cybersecurity operations.
 It’s no surprise to anyone that digital threats are evolving and becoming more complex than ever before. As attackers take their game to the next level, an organization’s cybersecurity program should grow and become smarter along with them. The latest step forward in digital defense comes in the form of machine learning and Artificial Intelligence algorithms that combine the reliability of traditional signatures with the power of Big Data analytics.
It’s no surprise to anyone that digital threats are evolving and becoming more complex than ever before. As attackers take their game to the next level, an organization’s cybersecurity program should grow and become smarter along with them. The latest step forward in digital defense comes in the form of machine learning and Artificial Intelligence algorithms that combine the reliability of traditional signatures with the power of Big Data analytics.
Legacy Tools No Longer the Answer to Growing Threats
With the ever-increasing sophistication of today’s security threats, traditional layers of defense like SIEMs, IDS/IPS, and antimalware applications are no longer sufficient. While these tools are certainly effective at thwarting routine port scans or spam emails, the smart security administrator needs to add another layer of security to be truly protected from advanced attacks. Signature-based defenses can’t scale fast enough or stay up to date with critical threats like zero-day attacks or a targeted phishing campaign, and reactive security programs are an open invitation for a data breach. While a business can add more resources to its SOC, or invest in the most engaging security awareness program, an organization’s defense is only as strong as the tools used in that defense. The reality is that security programs built on tools from as recent as 3-4 years ago are already outdated in the face of today’s threats.
Combining Traditional Defenses With Modern Data Analytics
What is the answer to the increasing complexity of these attacks? By pairing the usefulness of legacy solutions with a boost from Big Data, machine learning allows administrators to identify and prevent new or anomalous threats while controlling attacks from traditional threat vectors. Beginning with a baseline of signature files and a sample of normal activity from the network, new security devices can implement machine learning to automatically detect and shut down advanced threats that would otherwise slip past legacy perimeters.
An important component of these AI-driven devices is the ability to aggregate and analyze data from all the environments they are installed in, across multiple customers and industries. For clients who choose to opt-in to the program, smart devices can share their anonymized data in a pool of information from other clients, greatly increasing the samples that algorithms can be based upon. By analyzing data from such a large pool, these devices can leverage predictive analysis to protect an organization from threats that are new to their market but have been seen before in other industries.
In summary, security professionals should be aware that traditional lines of defense are no longer sufficient against today’s evolving threats. Machine intelligence and Big Data are changing the cybersecurity game by combining legacy methods with modern analysis and behavior models and should be seriously considered while building a well-rounded security program.
If you would like to learn more about machine learning in cybersecurity, click here to download "The Enterprise Immune System: Proven Mathematics and Machine Learning for Cyber Defense"...
PHOTO CREDIT: UNSPLASH | JASH CHHABRIA
Responding to Cybersecurity Threats: How to Assess Your Tools and Cyber Strategy
 Cybersecurity is in crisis. Cybersecurity threats are becoming increasingly sophisticated and pervasive. Bad actors have access to all the latest technology and tools, including artificial intelligence, for free or very little cost. They have endless time and resources to send out millions of cyberattacks – and need only a single successful attack to reap a windfall. It’s asymmetric warfare, and the attackers’ tools just keep improving.
Cybersecurity is in crisis. Cybersecurity threats are becoming increasingly sophisticated and pervasive. Bad actors have access to all the latest technology and tools, including artificial intelligence, for free or very little cost. They have endless time and resources to send out millions of cyberattacks – and need only a single successful attack to reap a windfall. It’s asymmetric warfare, and the attackers’ tools just keep improving.
In response, dozens of new cybersecurity providers seem to enter the market every day. Artificial intelligence, new tools and easy access to information mean that innovation keeps accelerating daily. With cybersecurity threats regularly making headlines, and pressure on companies to secure their data (and customers’ data) growing, new cybersecurity providers barely need to advertise to gain customers’ attention. For the same reasons, venture capitalists are eager to fund cybersecurity firms. The traditional big players in the market are rushing to upgrade their outdated packages. It’s a noisy marketplace, and companies trying to protect their data and systems are confused about how best to do so.
How Companies Are Addressing Cybersecurity Threats
Companies have responded to the crowded cybersecurity marketplace in different ways. Some just bury their heads in the sand, deciding to deal with incursions when they occur, or to hope that they’re too small to be worth targeting with a cyberattack. Others are spending way too much money on cybersecurity, experimenting with every new product that hits the market.
Many companies believe that they already have all the tools they need to combat cybersecurity threats, but haven’t properly patched their existing systems, which need regular updates to combat ever-changing cyber threats. On top of that, many companies experience dozens of little attacks every day, from all sides, and it’s hard to know where to put resources.
But burying your head in the sand or sticking with old tools that don’t counteract today’s cybersecurity threats is simply not an option. And throwing money at whatever strikes a chord isn’t an effective strategy, either.
What Is an Effective Strategy for Managing Cybersecurity Threats?
Resolving the cybersecurity crisis starts with an honest cyber vulnerability assessment, either by your internal experts or by outside experts.
Ultimately, this cyber vulnerability assessment should give you a map of where your company is in terms of cybersecurity. Next, you’ll need a map of where you’re going. Your experts should prepare a plan that:
- Closes your cybersecurity gaps over time
- Analyzes the financial risks of not closing gaps and prioritizes closing the gaps that put the company at the most risk
- Includes a company cybersecurity policy that every employee is expected to follow (much like a dress code or conduct policy)
This cyber vulnerability assessment and plan give you a framework for cybersecurity decisions. Armed with an understanding of your risk profile, your budget, your weaknesses and the consequences of various breaches, your experts should be able to recommend cybersecurity investments that will provide the best ROI for your company. The key is to remain true to this framework, even as new cybersecurity threats rear their ugly heads. Certainly, you want to maintain some flexibility, with strategies adjusting as truly required. But stick with what you know to be important to your business, and let that lead your investment decisions.
Wondering about your ability to respond to cybersecurity threats? Schedule a free, confidential assessment today.
 To thwart cyber attacks, the traditional approach has been to focus on the perimeter to repel intruders. But over time the perimeter has become a sieve. Today’s hackers easily break through it or find ways around it. In fact, a new study by RiskIQ estimates the cost cybercrime at $856,000 per minute. AI cybersecurity solutions directly address these challenges, which is why many now view the technology as the future of cybersecurity.
To thwart cyber attacks, the traditional approach has been to focus on the perimeter to repel intruders. But over time the perimeter has become a sieve. Today’s hackers easily break through it or find ways around it. In fact, a new study by RiskIQ estimates the cost cybercrime at $856,000 per minute. AI cybersecurity solutions directly address these challenges, which is why many now view the technology as the future of cybersecurity.
Going Beyond the Perimeter Is the Future of Cybersecurity
Focusing on defending the perimeter has been akin to wearing a Hazmat suit in a hostile environment: Any small perforation, and you were doomed to unexpected consequences at the hands of hackers who had the time and intellect to play games with your critical assets.
Not only are perimeters fragile and the gap in available talent huge, but most IT teams are often so stretched for resources that they can’t keep up with the updates necessary to protect against the myriad attacks that can penetrate a company’s external defenses. WannaCry was just an example of that.
Over the years, computing speed has grown exponentially –multiplying more than 3,000x since 1991 – to the point where even a $5 Raspberry Pi can now run deep learning algorithms. So it’s not a surprise that, in recent years, focus has shifted to using AI cybersecurity to complement traditional defenses in many ways and neutralize stealthy, unknown threats that may have already breached the perimeter before any irreparable damage to network or data is done.
Applying Artificial Intelligence in Cybersecurity
In AI cybersecurity programs, which are now being embedded in companies’ networks, endpoints and data are evolving into immune systems that allow internal defenses to shorten the dwell-time and pre-empt the devastation that can follow a breach.
While there is no need to abandon the perimeter, today’s smart CISOs are squarely focused on increasing their AI-driven pre-emption capabilities and boosting their own auto-immune systems. Artificial intelligence in cybersecurity is by no means perfect yet, but cybercriminals are already using automation and machine learning 24x7x365. In the never-ending cat-and-mouse game, AI is slated to continue gaining ground to build predictive capabilities and strengthen defenses for the foreseeable future.
To learn more about how AI is impacting the future of cybersecurity, download this white paper from Darktrace: Machine Learning in Cybersecurity.
ICS Cybersecurity: Using AI in Operational Technology Security
Updated on May 7, 2019
Recent headlines have been abuzz with ICS experts warning of grid vulnerability to hacking. Digital threat actors have become exceptionally skilled at infiltrating every type of computer network. Industrial Control Systems (ICS) are no different: While ICS networks were generally thought to be more secure due to not communicating outside of the corporate network or on the internet, attackers have managed to compromise them and steal valuable production data.
Some of the most effective tools for ICS cybersecurity are the emerging technologies in Machine Learning and Artificial Intelligence. By combining real-time data monitoring with orchestration and automated response, AI/ML solutions are proving their value when compared to legacy systems and human-intervention driven response times.
A Real-World Example of Using AI for ICS Network Security
At the 2017 Black Hat Europe conference, security research firm CyberX demonstrated how data exfiltration was possible from a supposedly air-gapped ICS network. By delivering a payload of specific ladder logic code into Programmable Logic Controllers, the attack was programmed to send out copies of data through encoded radio signals which can be received by AM radios and analyzed by special-purpose software. As the communication channel is outside the TCP/IP stack, there is no encryption to safeguard the data once it’s captured.
How does AI respond to this threat? In this case, Machine Learning can be used to craft an algorithm which establishes a “normal” state and monitors traffic and configurations to compare against that state. This baseline can include network traffic, equipment settings, and even the source code of PLCs. With its continuous heartbeat checks, the algorithm can detect when the system deviates from the baseline and immediately alert security staff of the change.
Another real-world example involving operational technology security comes very recently from the ransomware attack on Norsk Hyrdo, one of the world’s largest aluminum producers based in Norway. The ransomware infected multiple systems across the organization in a number of locations.The company’s production environments were forced to stop production or change to manual systems. The ransomware supported the changing of administrator passwords, and as the majority of servers were under the same domain, the attack could spread more rapidly than if there had been a combination of network segmentation and separately administered domains. In the case of Norsk, an AI cybersecurity layer would have been able to spot irregularities in system access and lockdown channels before the hackers could manipulate the permissions.
AI and ICS Cybersecurity: Adding Value to Existing Systems
Where does AI fit into your existing ICS network security program? You already have the ICS equipment sectioned off on its own VLAN(s), firewalled, monitored, and protected by IDS/IPS, SIEMs, and other security tools. Where does it make sense to insert AI/ML into the equation?
The biggest advantage of implanting an AI solution for ICS cybersecurity is its real-time response and orchestration. AI tools don’t need to wait for security staff to make a decision. They don’t see a black and white picture of firewall rules which often miss malware traffic flying under the radar, masquerading as “normal” network signals. Machine algorithms can detect abnormal data exchanges and immediately respond to the threat, long before a SOC resource would be alerted. Some AI offerings can even monitor devices that don’t communicate over TCP/IP, creating powerful visibility into non-networked equipment.
A particularly interesting tool to protect industrial control systems is Cyberbit’s ScadaShield, a layered solution to provide full stack ICS network detection, visibility, smart analytics, forensics and response. ScadaShield performs continuous monitoring and detection across the entire attack surface for both IT and OT components and can be combined with SOC automation to trigger workflows that accelerate root cause identification and mitigation.
Large-scale processes operating at critical power generation, electrical transmission, water treatment, and refining sites, as well as major manufacturing plants are more at risk than ever. The good news is that new developments in Artificial Intelligence and Machine Learning have created new ways to protect these systems and improve ICS cybersecurity.
If you haven’t already done so, this is a good time to consider adding an AI/ML solution to your security perimeter to take your prevention and response times to the next level. Click here to contact us if you would like to learn more about artificial intelligence in cyber security.
PHOTO CREDIT: UNSPLASH | RAMÓN SALINERO
Artificial Intelligence and ICS Cybersecurity: Filling Gaps in Operational Technology Security
 Recent headlines have been abuzz with ICS experts warning of grid vulnerability to hacking. Digital threat actors have become exceptionally skilled at infiltrating every type of computer network. Industrial Control Systems (ICS) are no different: While ICS networks were generally thought to be more secure due to not communicating outside of the corporate network or on the internet, attackers have managed to compromise them and steal valuable production data.
Recent headlines have been abuzz with ICS experts warning of grid vulnerability to hacking. Digital threat actors have become exceptionally skilled at infiltrating every type of computer network. Industrial Control Systems (ICS) are no different: While ICS networks were generally thought to be more secure due to not communicating outside of the corporate network or on the internet, attackers have managed to compromise them and steal valuable production data.
Some of the most effective tools for ICS cybersecurity are the emerging technologies in Machine Learning and Artificial Intelligence. By combining real-time data monitoring with orchestration and automated response, AI/ML solutions are proving their value when compared to legacy systems and human-intervention driven response times.
A Real-World Example of Using AI for ICS Network Security
At the last Black Hat Europe conference, security research firm CyberX demonstrated how data exfiltration was possible from a supposedly air-gapped ICS network. By delivering a payload of specific ladder logic code into Programmable Logic Controllers, the attack was programmed to send out copies of data through encoded radio signals which can be received by AM radios and analyzed by special-purpose software. As the communication channel is outside the TCP/IP stack, there is no encryption to safeguard the data once it’s captured.
How does AI respond to this threat? In this case, Machine Learning can be used to craft an algorithm which establishes a “normal” state and monitors traffic and configurations to compare against that state. This baseline can include network traffic, equipment settings, and even the source code of PLCs. With its continuous heartbeat checks, the algorithm can detect when the system deviates from the baseline and immediately alert security staff of the change.
Another real-world example involving operational technology security comes very recently from the ransomware attack on Atlanta’s municipal infrastructure, which involved encrypting city files, locking access to online services, and blocking the city from processing court cases and warrants. This is just the latest in a string of attacks on American cities. Previously, hackers gained access to Dallas’s tornado warning system and set off sirens in the middle of the night. In the case of Atlanta, an AI cybersecurity layer would have been able to spot irregularities in system access and lockdown channels before the hackers could manipulate the permissions.
AI and ICS Cybersecurity: Adding Value to Existing Systems
Where does AI fit into your existing ICS network security program? You already have the ICS equipment sectioned off on its own VLAN(s), firewalled, monitored, and protected by IDS/IPS, SIEMs, and other security tools. Where does it make sense to insert AI/ML into the equation?
The biggest advantage of implanting an AI solution for ICS cybersecurity is its real-time response and orchestration. AI tools don’t need to wait for security staff to make a decision. They don’t see a black and white picture of firewall rules which often miss malware traffic flying under the radar, masquerading as “normal” network signals. Machine algorithms can detect abnormal data exchanges and immediately respond to the threat, long before a SOC resource would be alerted. Some AI offerings can even monitor devices that don’t communicate over TCP/IP, creating powerful visibility into non-networked equipment.
A particularly interesting tool to protect industrial control systems is Cyberbit’s ScadaShield, a layered solution to provide full stack ICS networkdetection, visibility, smart analytics, forensics and response. ScadaShield performs continuous monitoring and detection across the entire attack surface for both IT and OT components and can be combined with SOC automation to trigger workflows that accelerate root cause identification and mitigation.
Large-scale processes operating at critical power generation, electrical transmission, water treatment, and refining sites, as well as major manufacturing plants are more at risk than ever. The good news is that new developments in Artificial Intelligence and Machine Learning have created new ways to protect these systems and improve ICS cybersecurity.
If you haven’t already done so, this is a good time to consider adding an AI/ML solution to your security perimeter to take your prevention and response times to the next level. Click here to get in touch with our team today.
PHOTO CREDIT: UNSPLASH | RAMÓN SALINERO
The Role of Artificial Intelligence in Cyber Security: Separating Fact from Fiction
 Machine learning and artificial intelligence have exploded onto the cybersecurity scene over the last year. Software vendors and MSSPs are scrambling to bring their particular flavor of AI cyber security to market and claim their stake as industry leaders.
Machine learning and artificial intelligence have exploded onto the cybersecurity scene over the last year. Software vendors and MSSPs are scrambling to bring their particular flavor of AI cyber security to market and claim their stake as industry leaders.
While AI has quickly become table stakes for an effective security posture, some of it can also seem to be overhyped in some respects. In this post, we’ll aim to cut through the superlatives and provide a few thoughts on the role of artificial intelligence in cyber security.
Artificial Intelligence in Cyber Security Does Not Replace Traditional Tools
By claiming that AI will replace traditional tools while lowering labor costs and probably making coffee at the same time, some advertising has put AI on a pedestal that it may not have achieved yet.
Here are some things that AI cyber security definitely will not replace. Security teams will still need to keep around:
- Employee training and a security-sensitive culture
- Smart policies and processes
- Qualified architects, managers, engineers, and analysts
- Rock-solid, layered infrastructure with effective controls around it
If you find yourself saying, “Wait, that’s 95% of my security program,” you’re right. Artificial intelligence in cyber security is a complement to a well-run cyber framework, not a replacement for it.
Must-Ask Questions When Evaluating AI Cyber Security Tools
We all have seen that technology can be promoted with grand promises backed by sometimes disappointing results. To avoid a dud in your AI implementation, you may want to sit down with your security team and your vendor rep to go over a few questions:
- How do your AI algorithms actually work? How mature is the technology? What are its blind spots?
- How well does it avoid false positives and false negatives?
- How do you measure the incremental benefits and the expected ROI?
- What outside support are we going to need to implement and maintain this?
- How much additional training will we need to use this effectively?
- Does it produce usable reports that actually mean something?
- What results have your other clients seen from it?
- Does it outperform what I already have, or will it be just another software bloating up my network?
Pitfalls to Avoid When Implementing an AI Cyber Security Solution
Adding software to your organization’s toolkit is rarely a trivial matter, and even less so when you’re dealing with AI. Here are some potential mistakes when deploying an AI cyber security tool:
- Expecting a “set-and-forget” solution that will replace the whole security program: See the first section of this post.
- Thinking that an in-house developed solution will be best-in-show without exploring other available options.
- Expecting that the AI tool won’t require any customization or integration.
- And possibly the most delicate one: Thinking it’ll all work out on automatic pilot without specialized AI expertise on your team or assistance from AI safety experts.
The fact of the matter is that it is no longer viable to delay implementation of robust AI cyber security tools. Bad actors have already started using AI.
A talented cybersecurity team and company-wide awareness trainings go a long way. Artificial intelligence in cyber security simply brings a needed support structure that can assist your teams to prevent attacks and accelerate mitigation if needed. As businesses undergo the digital transformation, it is imperative they also leverage new developments in cyber capabilities.
CyVent is a Certified Partner of Darktrace, a global leader in machine learning applied to cybersecurity, whose technology can detect and autonomously respond to cyber threats that legacy systems miss. Learn more about Darktrace’s capabilities in this white paper.
Updated on May 7, 2019
It’s no surprise to anyone that digital threats are evolving and becoming more complex than ever before. As attackers take their game to the next level, an organization’s cybersecurity program should grow and become smarter along with them. The latest step forward in digital defense comes in the form of machine learning and Artificial Intelligence algorithms that combine the reliability of traditional signatures with the power of Big Data analytics.
Legacy Tools No Longer the Answer to Growing Threats
With the ever-increasing sophistication of today’s security threats, traditional layers of defense like SIEMs, IDS/IPS, and antimalware applications are no longer sufficient. While these tools are certainly effective at thwarting routine port scans or spam emails, the smart security administrator needs to add another layer of security to be truly protected from advanced attacks. Signature-based defenses can’t scale fast enough or stay up to date with critical threats like zero-day attacks or a targeted phishing campaign, and reactive security programs are an open invitation for a data breach. While a business can add more resources to its SOC, or invest in the most engaging security awareness program, an organization’s defense is only as strong as the tools used in that defense. The reality is that security programs built on tools from as recent as 3-4 years ago are already outdated in the face of today’s threats.
Combining Traditional Defenses With Modern Data Analytics
What is the answer to the increasing complexity of these attacks? By pairing the usefulness of legacy solutions with a boost from Big Data, machine learning allows administrators to identify and prevent new or anomalous threats while controlling attacks from traditional threat vectors. Beginning with a baseline of signature files and a sample of normal activity from the network, new security devices can implement machine learning to automatically detect and shut down advanced threats that would otherwise slip past legacy perimeters.
An important component of these AI-driven devices is the ability to aggregate and analyze data from all the environments they are installed in, across multiple customers and industries. For clients who choose to opt-in to the program, smart devices can share their anonymized data in a pool of information from other clients, greatly increasing the samples that algorithms can be based upon. By analyzing data from such a large pool, these devices can leverage predictive analysis to protect an organization from threats that are new to their market but have been seen before in other industries.
In summary, security professionals should be aware that traditional lines of defense are no longer sufficient against today’s evolving threats. Machine intelligence and Big Data are changing the cybersecurity game by combining legacy methods with modern analysis and behavior models and should be seriously considered while building a well-rounded security program. Click here to learn more about machine learning in cyber security.
PHOTO CREDIT: UNSPLASH | JASH CHHABRIA
Updated on May 7, 2019
Every other day, we hear disclosures about some new security breach that leads to damaged reputations, executive resignations and plummeting stock values. While It is tempting to become a wee-bit sarcastic and ‘normalize’ this state of affairs, the danger of cyber attacks can’t be understated. The gap between time to exfiltration vs time to quarantine is growing in favor of attackers. Thought leaders and Trillion-Dollar loss projections reinforce that information warfare is a serious threat that’s quickly becoming the #1 danger for businesses, governments and even individual liberties.
What is the Role of Cybersecurity?
Throw in a dizzying array of new technologies and new vendors, and it‘s no wonder cyber security executives, CFOs and CEO’s feel growing levels of pressure. What we all need at this time is a change in attitude: The role of cyber security is to enable the business to reach its goals, not to be the goal in and of itself. No business exists for the sake of having an unbreachable security program, if such a thing can even be built. On the contrary, a good security program drives and supports the organization to reach its strategic goals.
In this non-stop ‘spy vs. spy’ game between good guys and bad actors, the solution is not to keep adding one shiny tool after another but rather focusing on a well-thought out strategy that includes multiple prongs: (a) Periodic audits, strong fundamentals, clear policies and well-trained team members (b) adding advanced tools to automate, orchestrate and streamline processes while reducing costs, and (c) including cyber security within the C-level risk management view that balances acceptable exposure levels, qualifies the required investments and takes advantage of available risk transfer options.
What is the role of a trusted Cyber Security Solutions Provider?
Within this quickly changing environment, a trusted partner’s role is to help the clients reduce anxiety, become better risks and increase peace of mind.
A trustworthy partner will sit down and fully understand your needs before talking about any kind of product lineup. If you have security questions, contact us and let’s make a plan that works for you.
PHOTO CREDIT: UNSPLASH | TASKIN ASHIQ
The Importance of a Cyber Security Program Built on Strategy, Not Fear
 Every other day, we hear disclosures about some new security breach that leads to damaged reputations, executive resignations and plummeting stock values. While It is tempting to become a wee-bit sarcastic and ‘normalize’ this state of affairs, the danger of cyber attacks can’t be understated. The gap between time to exfiltration vs time to quarantine is growing in favor of attackers. Thought leaders and Trillion-Dollar loss projections reinforce that information warfare is a serious threat that’s quickly becoming the #1 danger for businesses, governments and even individual liberties.
Every other day, we hear disclosures about some new security breach that leads to damaged reputations, executive resignations and plummeting stock values. While It is tempting to become a wee-bit sarcastic and ‘normalize’ this state of affairs, the danger of cyber attacks can’t be understated. The gap between time to exfiltration vs time to quarantine is growing in favor of attackers. Thought leaders and Trillion-Dollar loss projections reinforce that information warfare is a serious threat that’s quickly becoming the #1 danger for businesses, governments and even individual liberties.
What is the Role of Cybersecurity?
Throw in a dizzying array of new technologies and new vendors, and it‘s no wonder cyber security executives, CFOs and CEO’s feel growing levels of pressure. What we all need at this time is a change in attitude: The role of cyber security is to enable the business to reach its goals, not to be the goal in and of itself. No business exists for the sake of having an unbreachable security program, if such a thing can even be built. On the contrary, a good security program drives and supports the organization to reach its strategic goals.
In this non-stop ‘spy vs. spy’ game between good guys and bad actors, the solution is not to keep adding one shiny tool after another but rather focusing on a well-thought out strategy that includes multiple prongs: (a) Periodic audits, strong fundamentals, clear policies and well-trained team members (b) adding advanced tools to automate, orchestrate and streamline processes while reducing costs, and (c) including cyber security within the C-level risk management view that balances acceptable exposure levels, qualifies the required investments and takes advantage of available risk transfer options.
What is the role of a trusted Cyber Security Solutions Provider?
Within this quickly changing environment, a trusted partner’s role is to help the clients reduce anxiety, become better risks and increase peace of mind.
A trustworthy partner will sit down and fully understand your needs before talking about any kind of product lineup. If you have security questions, contact us and let’s make a plan that works for you.


.png?width=750&height=201&name=Untitled%20(1).png)









